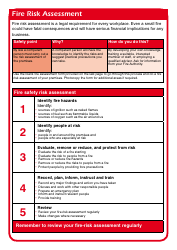
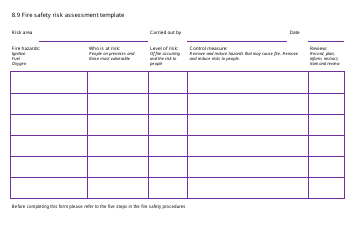
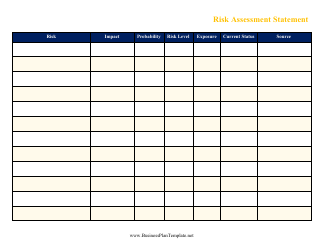
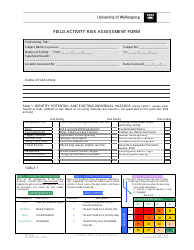
Vulnerability Assessment Template
A Vulnerability Assessment Template is used to identify and evaluate potential weaknesses or vulnerabilities in a system or organization. It helps to assess the security risks and identify areas that need improvement in order to enhance the overall security posture.
The Vulnerability Assessment Template is typically filed by the organization or entity conducting the assessment.
FAQ
Q: What is a vulnerability assessment?
A: A vulnerability assessment is a process of identifying, quantifying, and prioritizing vulnerabilities in a system.
Q: Why do I need a vulnerability assessment?
A: A vulnerability assessment helps to identify weaknesses in your system or network that could be exploited by attackers.
Q: What is included in a vulnerability assessment template?
A: A vulnerability assessment template provides a framework for conducting a thorough assessment, including steps to follow and areas to evaluate.
Q: How often should I conduct a vulnerability assessment?
A: It is recommended to conduct vulnerability assessments on a regular basis, at least annually or whenever significant changes are made to the system.
Q: Who should conduct a vulnerability assessment?
A: A qualified professional or a team with expertise in cybersecurity should perform a vulnerability assessment.
Q: What are the benefits of a vulnerability assessment?
A: Some benefits of a vulnerability assessment include identifying and mitigating potential security risks, enhancing the overall security posture, and complying with industry standards and regulations.
Q: What are some common vulnerabilities that are assessed?
A: Common vulnerabilities that are assessed include weak passwords, outdated software, unpatched systems, misconfigurations, and insecure network protocols.
Q: How long does a vulnerability assessment take?
A: The duration of a vulnerability assessment can vary depending on the complexity of the system and the scope of the assessment. It could range from a few days to several weeks.
Q: What should I do after a vulnerability assessment?
A: After a vulnerability assessment, it is important to address the identified vulnerabilities by implementing appropriate security measures and fixes.
Q: Can I perform a vulnerability assessment on my own?
A: While it is possible to perform a vulnerability assessment on your own, it is recommended to seek the assistance of a professional to ensure thoroughness and accuracy of the assessment.