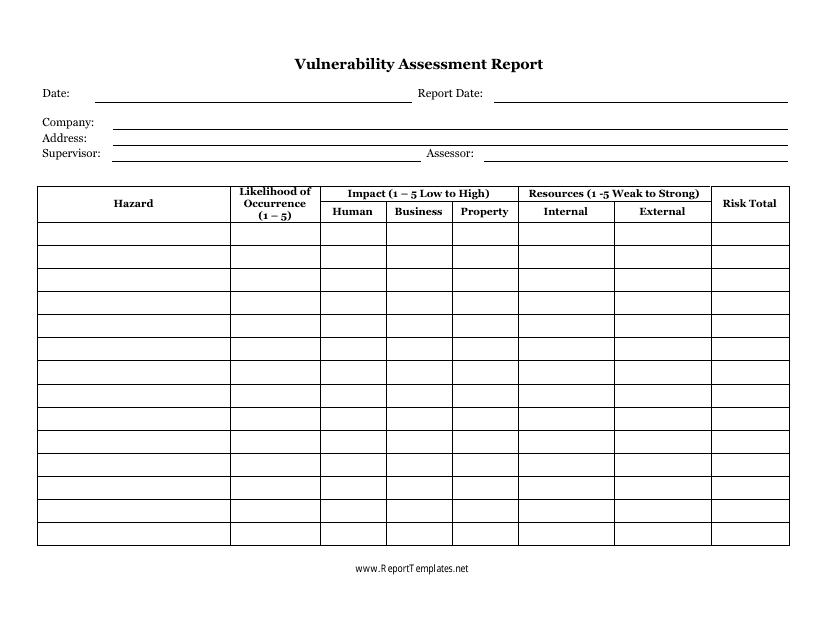
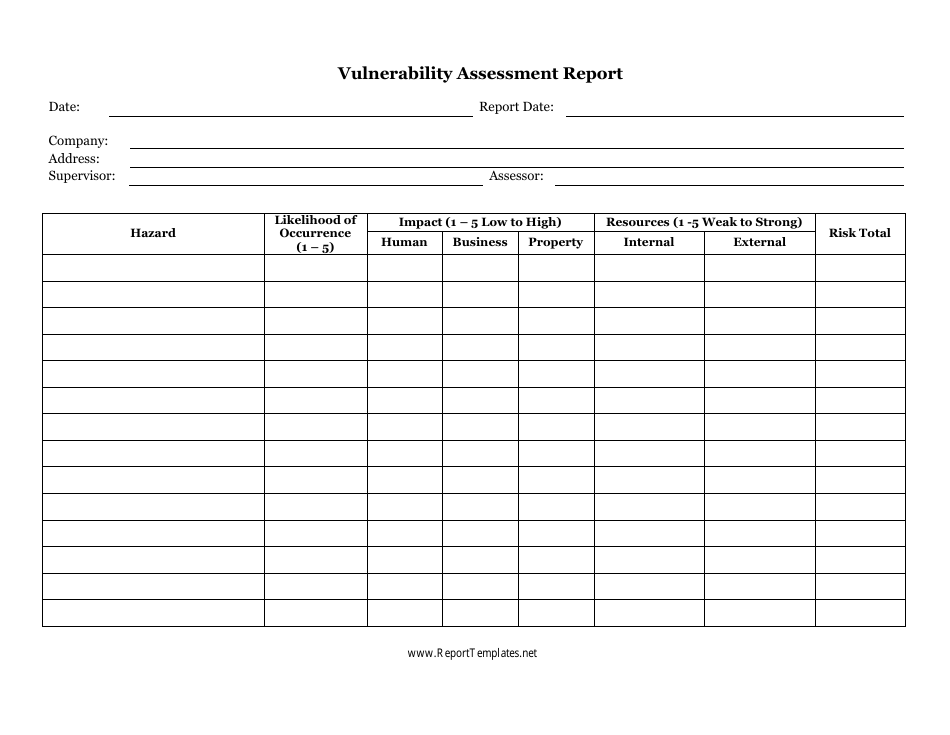
Vulnerability Assessment Report Template
A Vulnerability Assessment Report Template is used to evaluate the security vulnerabilities present in a system, network, or infrastructure. It helps identify potential weaknesses and provides recommendations for improving security measures.
FAQ
Q: What is a Vulnerability Assessment Report?
A: A Vulnerability Assessment Report is a document that identifies and evaluates the vulnerabilities in a system or network.
Q: Why is a Vulnerability Assessment Report important?
A: A Vulnerability Assessment Report is important because it helps identify potential weaknesses in a system or network that could be exploited by attackers.
Q: What does a Vulnerability Assessment Report include?
A: A Vulnerability Assessment Report typically includes a summary of findings, a list of vulnerabilities, their severity levels, and recommendations for addressing them.
Q: Who performs a Vulnerability Assessment?
A: A Vulnerability Assessment is typically performed by a security professional or a team of professionals who specialize in assessing and identifying vulnerabilities.
Q: How often should a Vulnerability Assessment be performed?
A: A Vulnerability Assessment should be performed regularly, ideally on a scheduled basis, to ensure that any new vulnerabilities are identified and addressed.
Q: What are the benefits of conducting a Vulnerability Assessment?
A: Some benefits of conducting a Vulnerability Assessment include identifying and mitigating potential security risks, maintaining compliance with industry regulations, and improving overall system security.
Q: What is the difference between a Vulnerability Assessment and a Penetration Test?
A: A Vulnerability Assessment focuses on identifying vulnerabilities, while a Penetration Test goes a step further to actively exploit those vulnerabilities to assess the system's resilience against attacks.
Q: How can I use a Vulnerability Assessment Report?
A: A Vulnerability Assessment Report can be used to prioritize and address vulnerabilities, allocate resources for security improvements, and communicate the overall security posture to stakeholders.
Q: Can a Vulnerability Assessment guarantee complete security?
A: No, a Vulnerability Assessment cannot guarantee complete security as new vulnerabilities can emerge over time. However, it helps in identifying and mitigating known vulnerabilities.
Q: What are some common vulnerabilities that a Vulnerability Assessment can identify?
A: Common vulnerabilities that a Vulnerability Assessment can identify include outdated software, weak passwords, misconfigured settings, and unpatched systems.