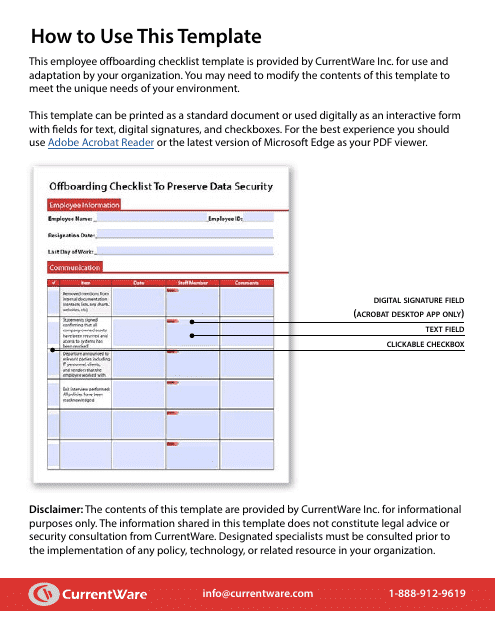
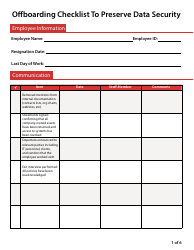
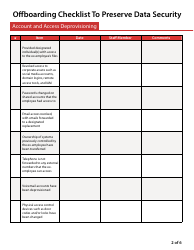
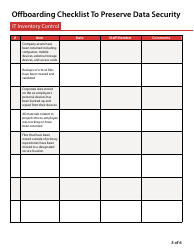
Offboarding Checklist to Preserve Data Security
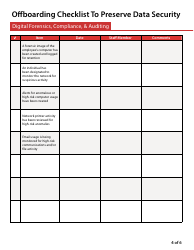
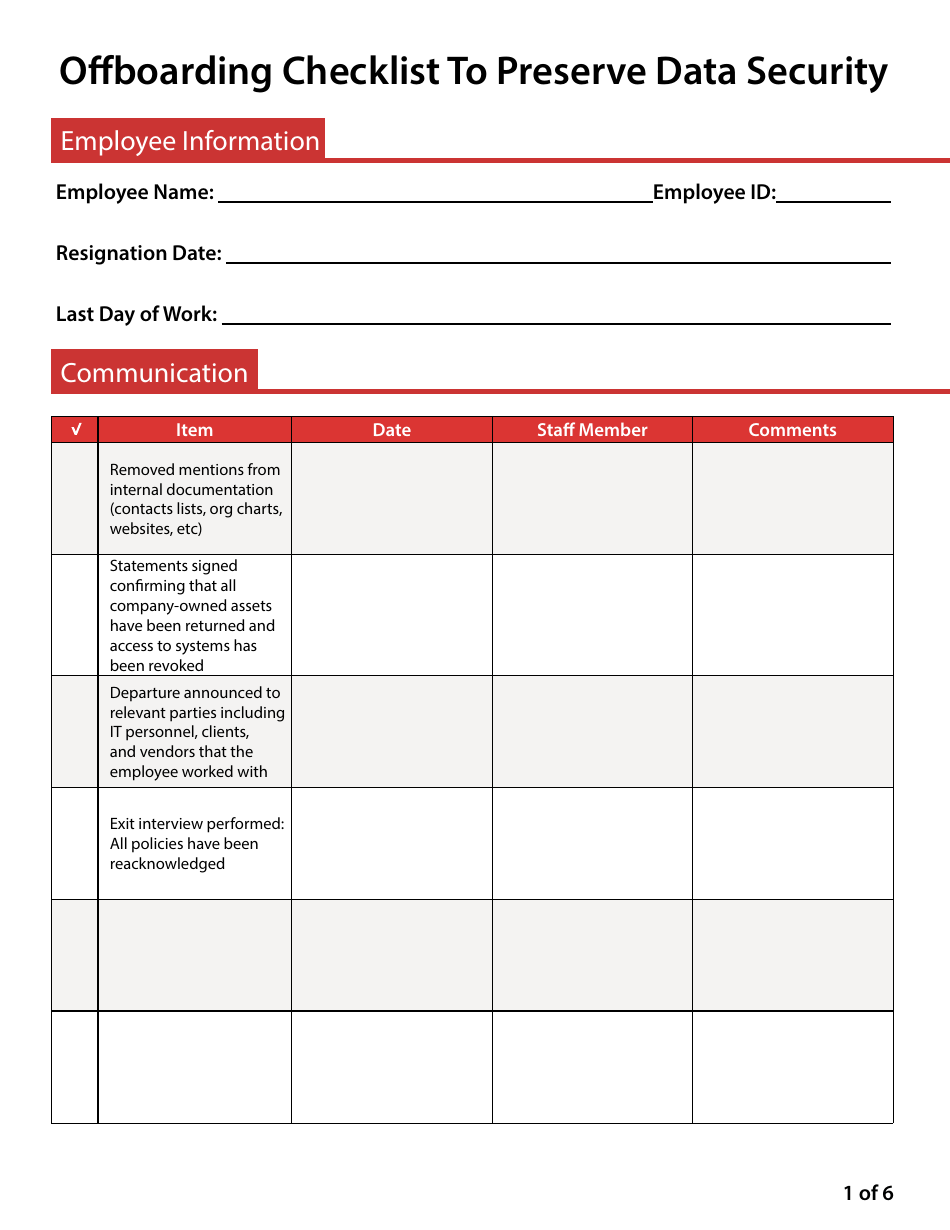
The Offboarding Checklist to Preserve Data Security is for ensuring that a company's data and informational assets are protected when an employee leaves the organization. It outlines a systematic process to recover the company property, deactivate employee access to work files, databases, emails, and other confidential resources of the organization to maintain data security. This checklist is crucial in preventing unauthorized access, data breaches, or potential misuse of business information.
The responsibility of filing the Offboarding Checklist to Preserve Data Security primarily lies with the company's Human Resources (HR) Department. This process involves detailing the steps for removing access points, retrieving company assets, and ensuring sensitive information remains secure when an employee leaves the company. However, it's also important for the IT department to be involved to handle the technical aspects of the offboarding process. The exact individuals or teams may vary depending on the company's structure and protocol.
FAQ
Q: What is an offboarding checklist for preserving data security?
A: An offboarding checklist for preserving data security is a set of tasks to safely transfer or delete an employee's digital and physical access to company assets when they leave. Tasks might include revoking network access, returning company property, and deleting email accounts.
Q: Why is an offboarding checklist important for data security?
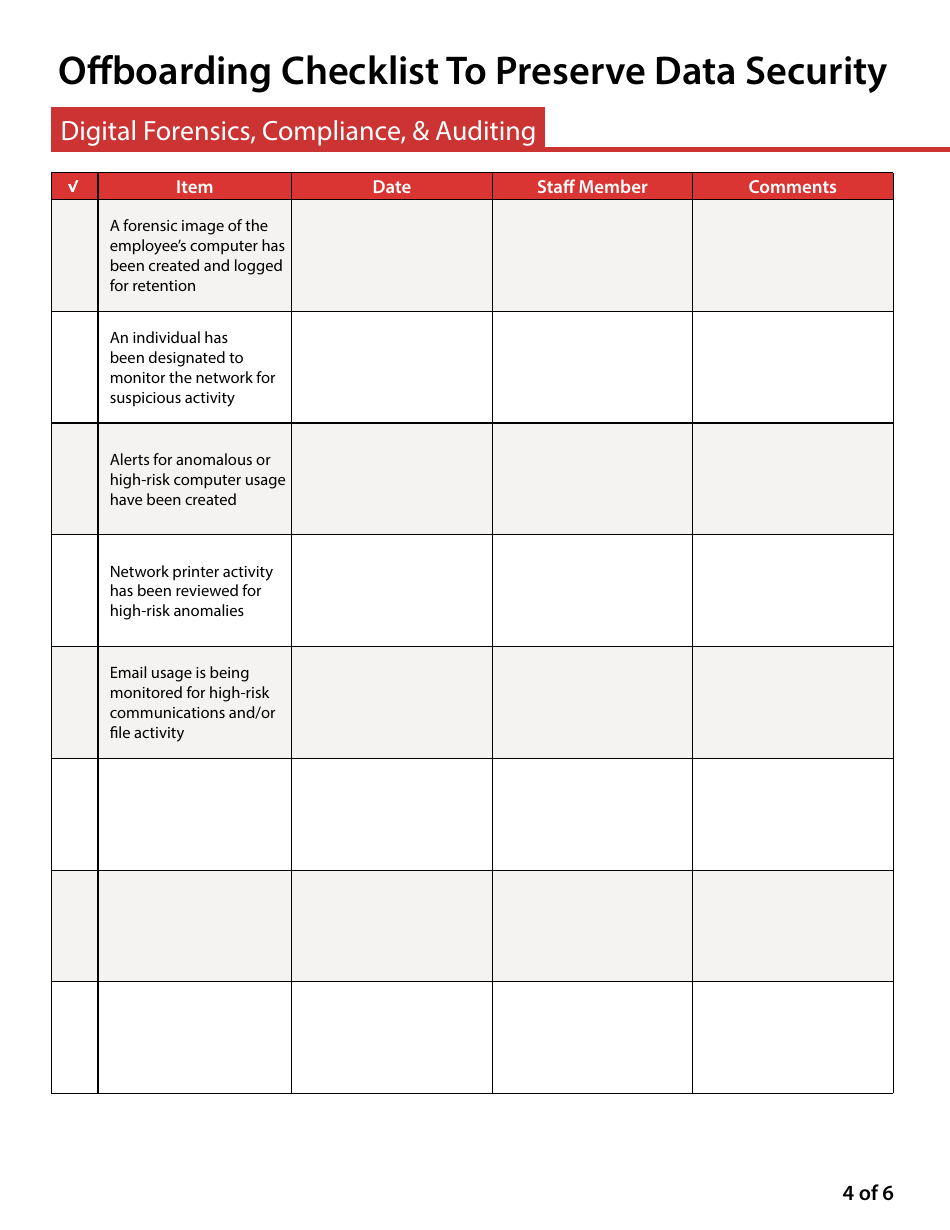
A: An offboarding checklist is a proactive measure to prevent data breaches, protect intellectual property, and preserve company's reputation. Proper offboarding guards against accidental or intentional theft, misuse, or corruption of company's resources or data by departed employees.
Q: What steps are involved in an offboarding data security checklist?
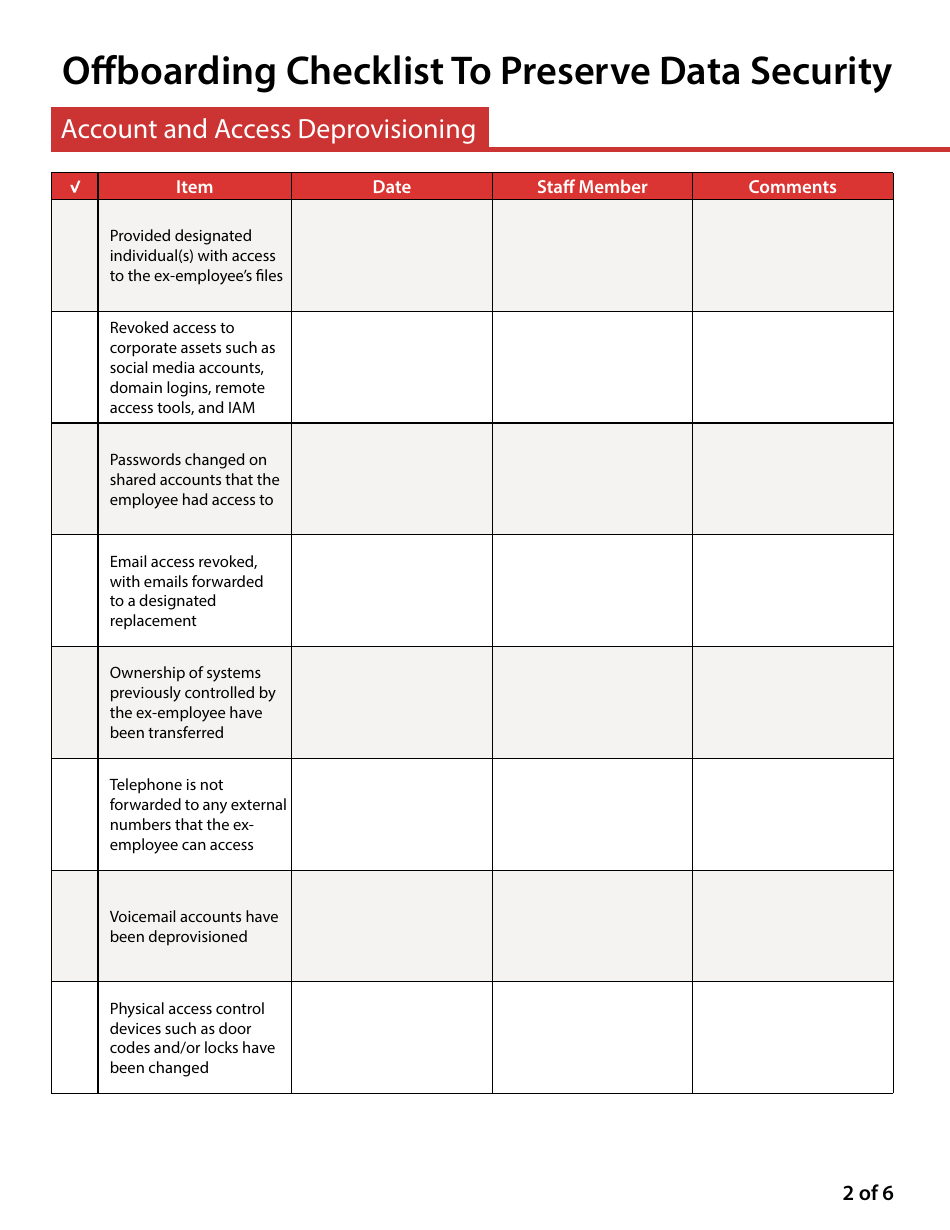
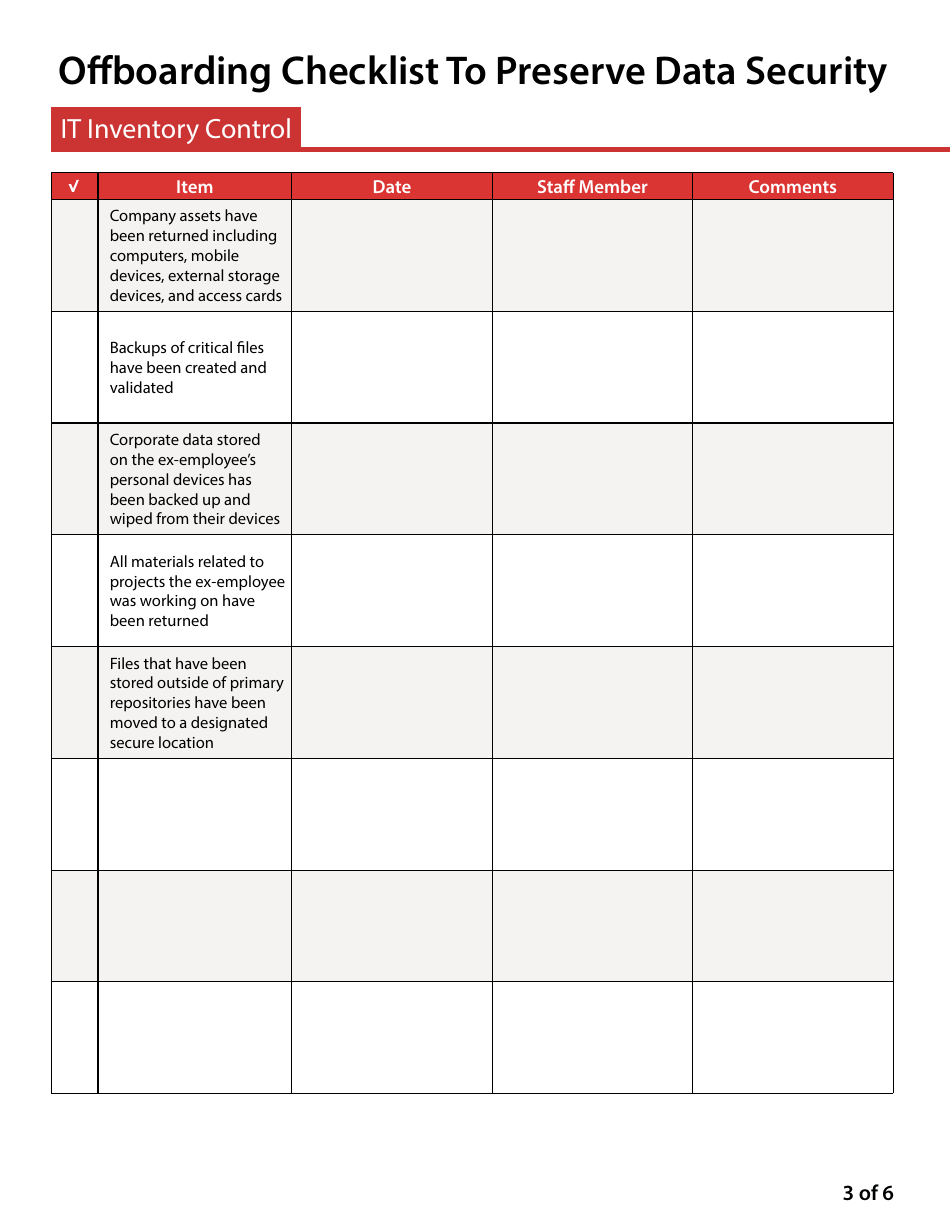
A: Steps usually involve: 1) Revoking digital access to company networks and accounts. 2) Deleting or securing the ex-employee's email account. 3) Cleaning up any company data from their personal devices. 4) Retrieving all company property. 5) Confirming that no company data has been downloaded or transferred elsewhere.
Q: Who is responsible for ensuring the offboarding data security checklist is completed?
A: The responsibility is usually shared across HR, IT, and the employee's direct supervisor. They collectively ensure all steps are completed, protecting company's data and resources.
Q: How are individual countries handling offboarding data security?
A: In the USA, companies often follow a strict offboarding process that includes elements of data security. In Canada, the Personal Information Protection and Electronic Documents Act guides businesses on data protection. In India, governed by the Information Technology Act, companies must ensure sensitive data protection during employee offboarding. In Australia, the Privacy Act mandates data protection in such scenarios.