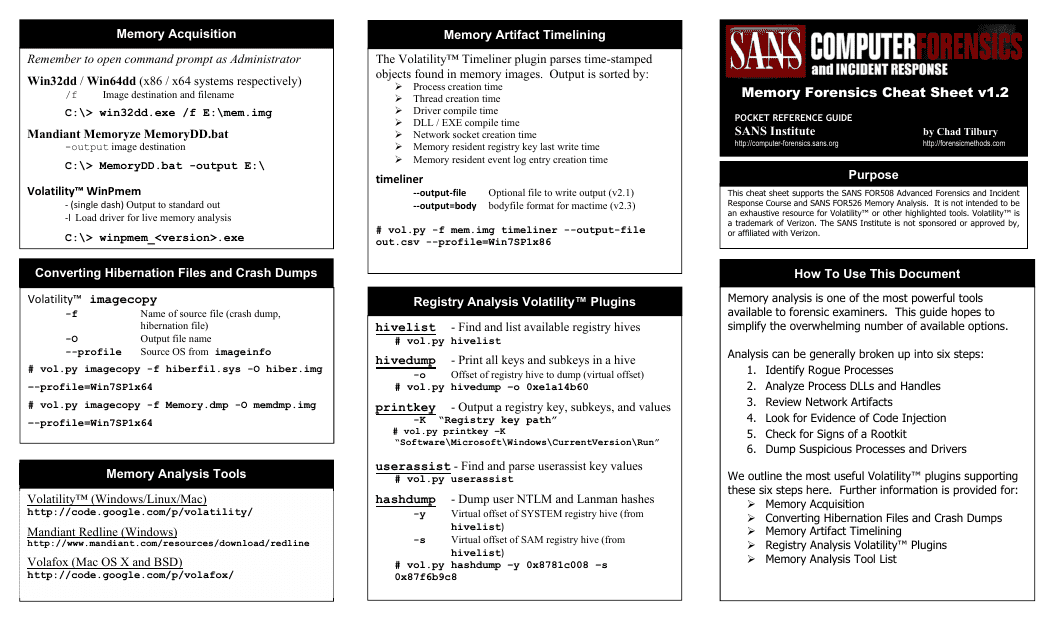
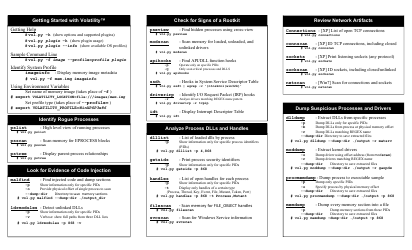
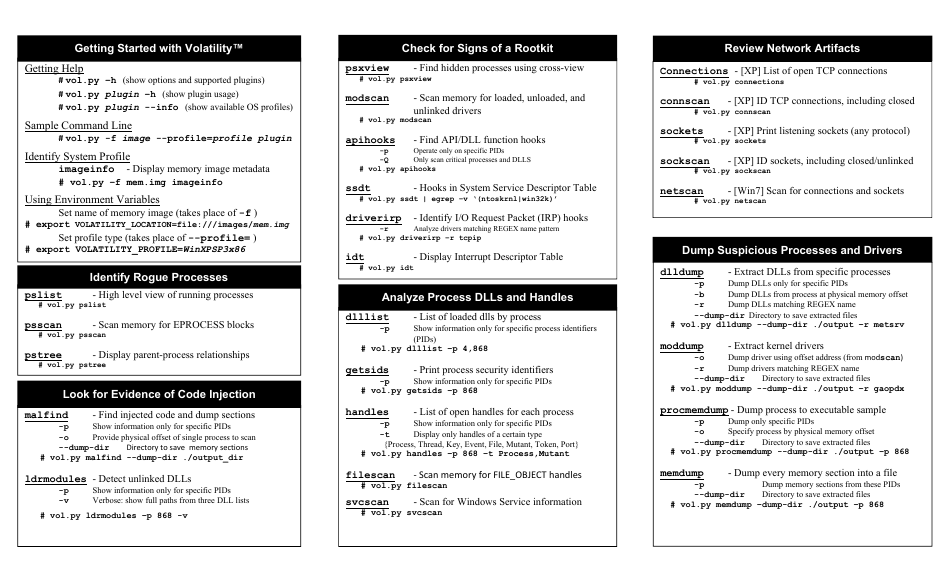
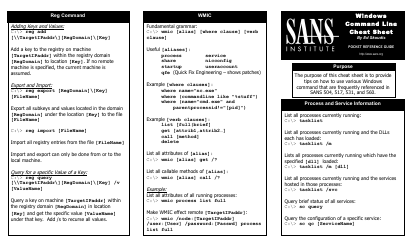
Memory Forensics Cheat Sheet V1.2 - Sans Computer Forensics
Memory Forensics Cheat Sheet V1.2 - SANS Computer Forensics is a resource that provides helpful information and techniques for conducting forensic analysis on computer memory (RAM). It can be used by forensic investigators to uncover evidence, analyze malicious activities, and understand the state of a system at a particular point in time.
The Memory Forensics Cheat Sheet V1.2 is filed by the SANS Institute, specifically their Computer Forensics department.
FAQ
Q: What is memory forensics?
A: Memory forensics is the process of analyzing and extracting data from a computer's volatile memory.
Q: Why is memory forensics important?
A: Memory forensics can uncover valuable information that may not be accessible through traditional disk-based forensics.
Q: What can be recovered from memory?
A: Memory can contain information such as passwords, open files, network connections, and evidence of malware or malicious activity.
Q: How is memory forensics conducted?
A: Memory forensics involves using specialized tools and techniques to acquire and analyze a computer's volatile memory.
Q: What are some popular memory forensics tools?
A: Some popular memory forensics tools include Volatility, Rekall, and DumpIt.
Q: What are the challenges of memory forensics?
A: Challenges of memory forensics include volatility of data, potential encryption, and the need for specialized knowledge and skills.
Q: What are some applications of memory forensics?
A: Memory forensics can be used for incident response, malware analysis, investigating computer breaches, and detecting unauthorized activities.
Q: Are there legal considerations for memory forensics?
A: Yes, conducting memory forensics must comply with legal and privacy regulations, and proper documentation and chain of custody must be maintained.
Q: Is memory forensics applicable to both Windows and Mac systems?
A: Yes, memory forensics can be applied to both Windows and Mac systems, as well as other operating systems.
Q: Are there any limitations to memory forensics?
A: Some limitations of memory forensics include data volatility, limited time window for analysis, and the need for physical access to the memory.