It Risk Assessment Template
What Is IT Risk Assessment?
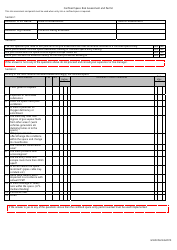
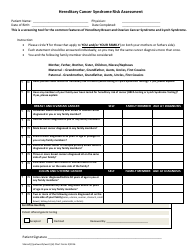
An IT Risk Assessment Template is a written analysis of the IT systems of an organization prepared to detect the existing and potential flaws and implement protective measures that will keep the entity safe. Use this document if you need to identify sources of threats to your business, evaluate safety protocols already in place, establish which assets may be in danger, and calculate the funds necessary to protect the business from cybersecurity issues.
Alternate Name:
- IT Security Risk Assessment.
Whether you manage a small business or a large corporation, it is the duty of the company administrators and IT department to learn more about the weak points of current security protocols and conduct a risk assessment. You may download an IT Risk Assessment template through the link below.
How to Perform an IT Risk Assessment?
There are two main types of the IT Risk Assessment methodology:
- Quantitative method - focus on the potential risks and digital information you want to protect most. Make a list of assets and indicate their approximate value. This will show you how much you would lose in case of a security breach and you will be able to relocate funds to defend the integrity of confidential data.
- Qualitative method - concentrate on the company personnel to find out more about their day-to-day operations and learn which aspects of their job should be prioritized. Interview all the employees that work with sensitive information, make a list of devices they use to handle this data, and correctly evaluate the systems and units that may be vulnerable to outside attacks.
Once you have chosen the methodology - and it may be a good idea to implement both of them - follow this IT Risk Assessment Checklist to protect the interests of your organization:
- Prepare to document all the data assets of the business . It includes not only the electronic files that can be accessed via computers of employees, but also hard copies and internal records you keep in the archive, telephones and laptops.
- Instruct the employee in charge of IT security to make a list of potential violations and breaches . For instance, a member of your staff may lose their phone - consider protecting all the valuable information with passwords and multi-factor authentication.
- Apply security protocols to decrease the likelihood of risk . You may update the existing measures or implement new procedures that safeguard the company and third parties whose data may be stored on your computers and in your records.
Why Is It Important to Do a Risk Assessment?
The purpose of IT Risk Assessment is to reduce the risks of security breaches and compliance issues. Every organization should invest in proper risk assessment for several reasons:
- Protect the business from unauthorized access to its digital data, networks, and devices . You need to make sure the company is safeguarded against cyberattacks which is extremely important if your entity handles large amounts of confidential information.
- Determine the areas and departments that require better protection . It may be unreasonable to spend a lot of money to update the security measures all over the company especially if the entity is small and you do not have funds for that at the moment. However, a proper evaluation of risks will show you the vulnerabilities of the business and you can set priorities and invest sensibly.
- Comply with the legal requirements of the state and county . Depending on your location, you may be compelled to follow regulations regarding the documentation of risk assessments and standards of privacy, so make sure you keep up with the latest updates to relevant legislation to avoid fines.
Haven't found the template you're looking for? Take a look at the related templates below: