Recommended Practice: Improving Industrial Control Systems Cybersecurity With Defense-In-depth Strategies
Recommended Practice: Improving Industrial Control Systems Cybersecurity With Defense-In-depth Strategies is a 44-page legal document that was released by the U.S. Department of Homeland Security on October 1, 2009 and used nation-wide.
FAQ
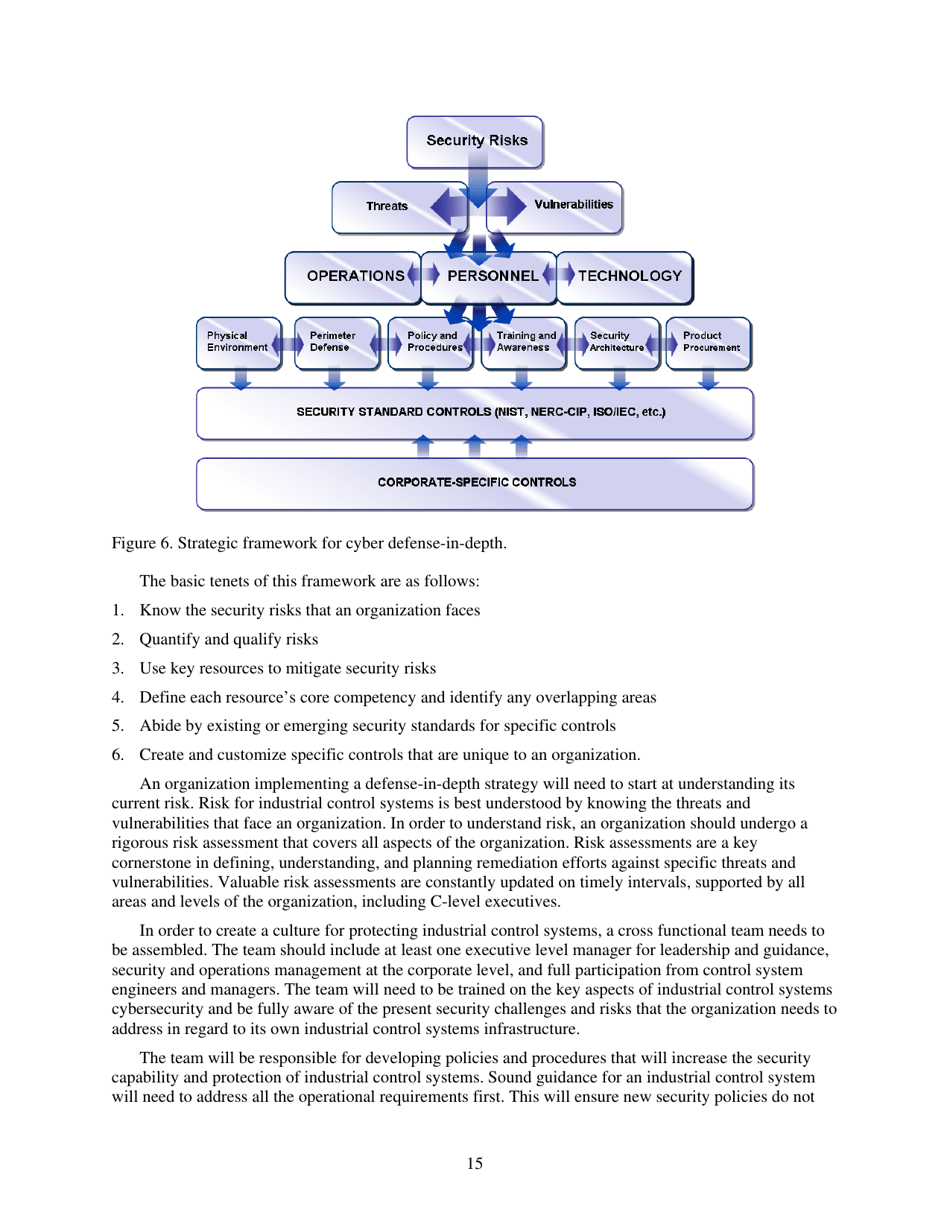
Q: What is defense-in-depth?
A: Defense-in-depth is a cybersecurity strategy that uses multiple layers of security controls to protect industrial control systems.
Q: Why is defense-in-depth important for industrial control systems?
A: Defense-in-depth is important for industrial control systems because they are often targeted by cyber threats and a single layer of security may not be sufficient to protect them.
Q: What are some examples of defense-in-depth strategies?
A: Examples of defense-in-depth strategies include network segmentation, access control, intrusion detection systems, and regular security assessments.
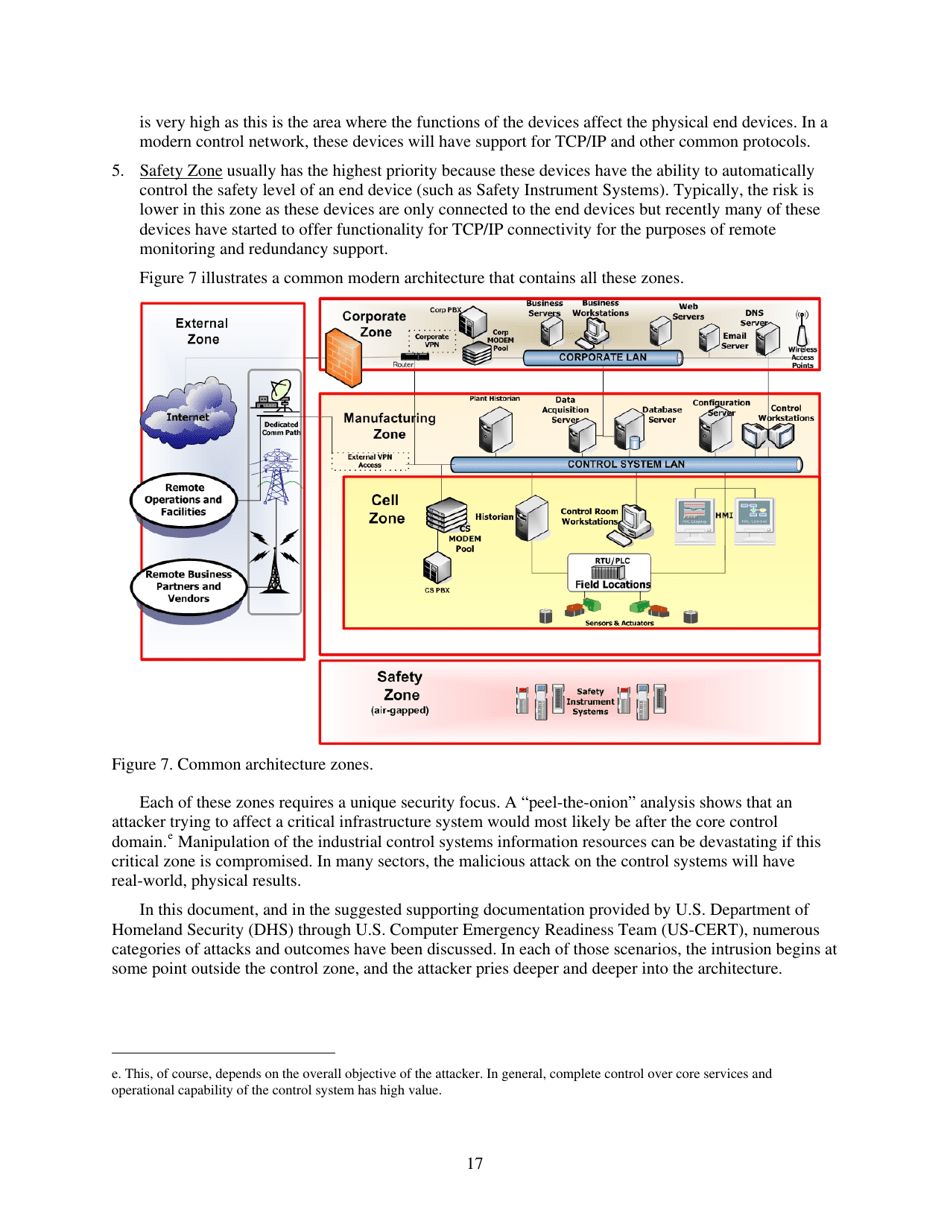
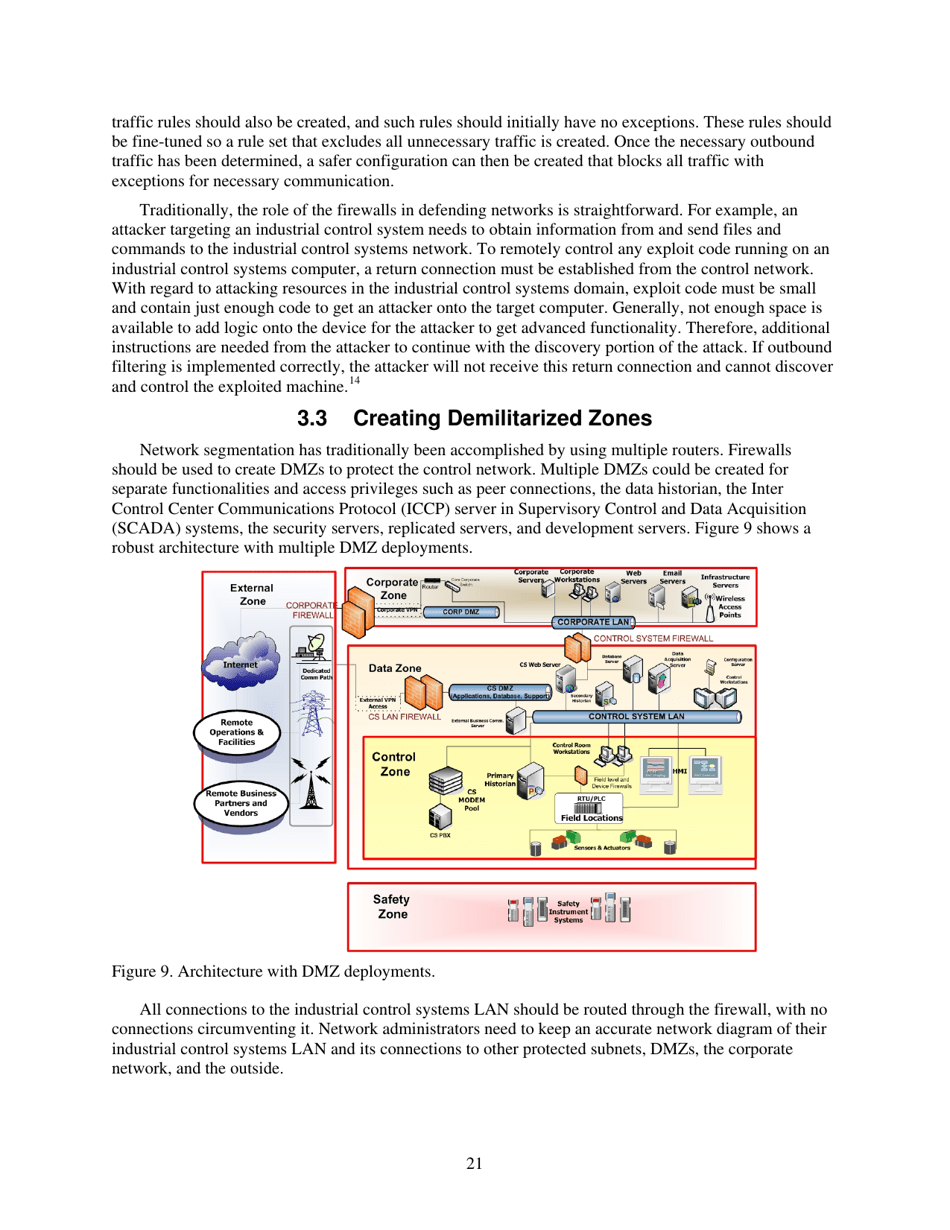
Q: Why is network segmentation a part of defense-in-depth?
A: Network segmentation helps to isolate critical systems, limit the impact of a cyber attack, and prevent lateral movement within the network.
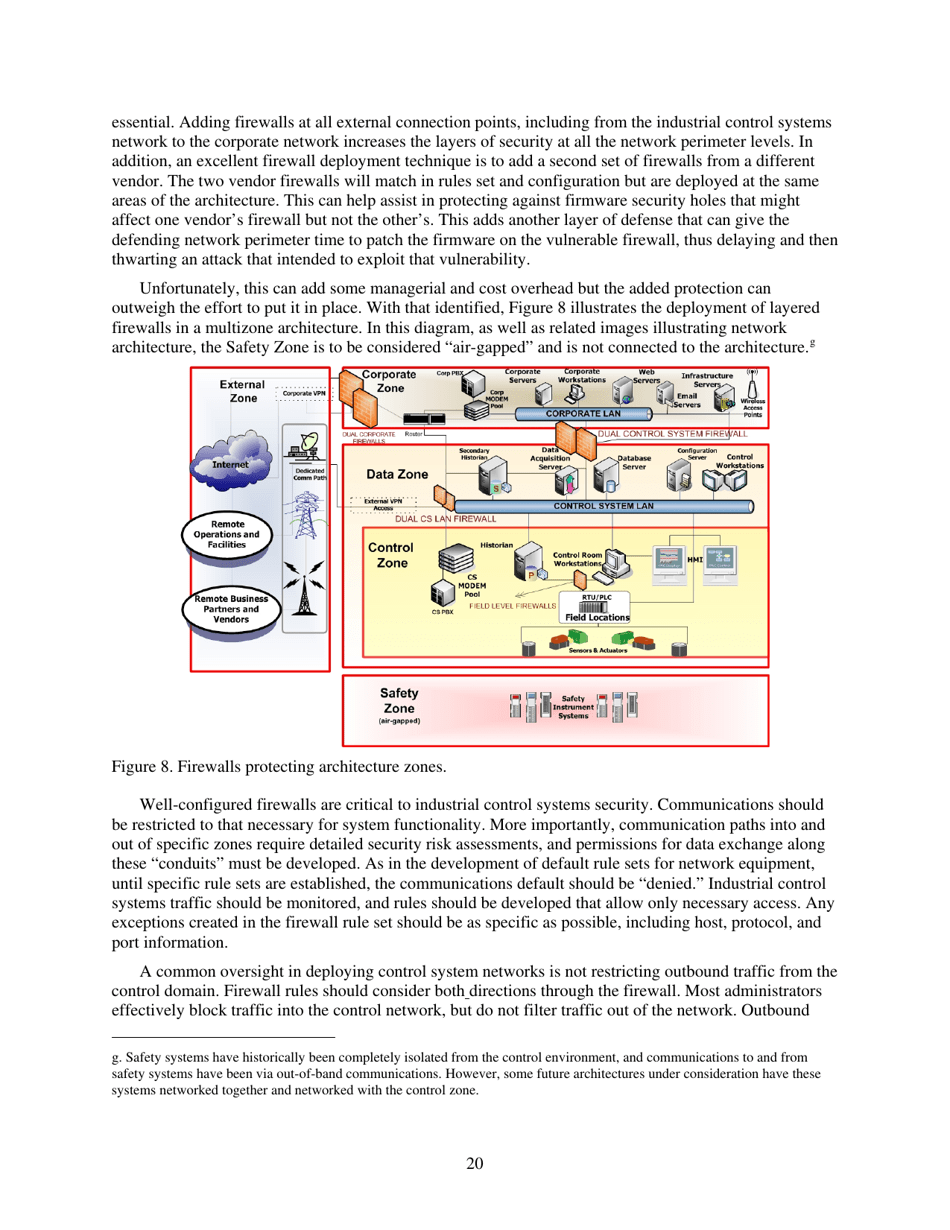
Q: What is the role of access control in defense-in-depth?
A: Access control ensures that only authorized individuals have access to critical systems and resources, reducing the risk of unauthorized access or malicious activity.
Q: What is an intrusion detection system?
A: An intrusion detection system is a security technology that monitors network traffic for suspicious activity or known attack patterns.
Q: Why are regular security assessments important in defense-in-depth?
A: Regular security assessments help to identify vulnerabilities and weaknesses in the system, allowing for timely remediation and improvement of security measures.
Form Details:
- The latest edition currently provided by the U.S. Department of Homeland Security;
- Ready to use and print;
- Easy to customize;
- Compatible with most PDF-viewing applications;
- Fill out the form in our online filing application.
Download a printable version of the form by clicking the link below or browse more legal forms and templates provided by the issuing department.