Access Control Templates
Access Control: Ensuring Security and Safety
In today's rapidly changing world, it is more important than ever to maintain strict control over access to sensitive areas and resources. Access control, also known as controlled access or access controls, refers to the rigorous procedures and systems implemented to regulate entry and monitor the movement of individuals within an organization or facility.
With multiple access points and increasing concerns about unauthorized access, organizations must stay vigilant in protecting their assets, from information to physical spaces. Access control measures, such as access control forms, have become crucial components in managing and maintaining security.
Access control forms facilitate various processes, including disabling or removing access for individuals who no longer require access privileges or whose access cards have been lost or misplaced. Furthermore, access control forms allow for efficient reporting and documentation of access events, ensuring the necessary accountability and transparency.
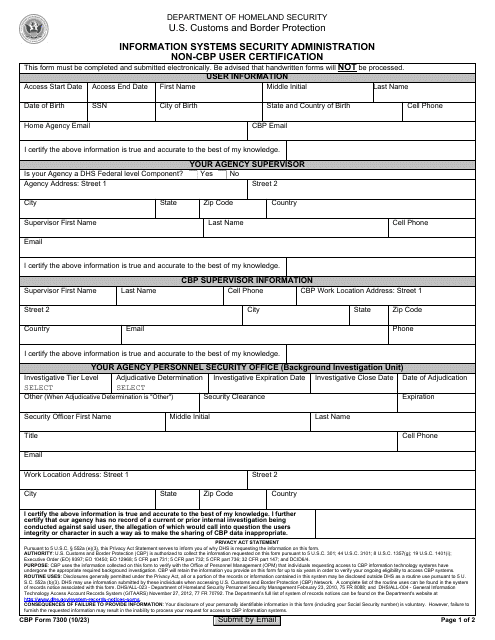
One of the essential documents related to access control is the AF Form 106 Sensitive Compartmented Information (SCI) Access Certification, which plays a vital role in managing access to classified information within the United States Air Force.
In addition to this, various other documentation contributes to the effective implementation of access control systems. For instance, the ACS Access Control System Notification, known as Form ACS, is utilized in monitoring access to specific areas or buildings in the state of Montana. Furthermore, the AE Form 190-16H Installation Access Control System (IACS) Deny Access Letter is essential for denying access to personnel who do not meet the necessary requirements or have violated security protocols.
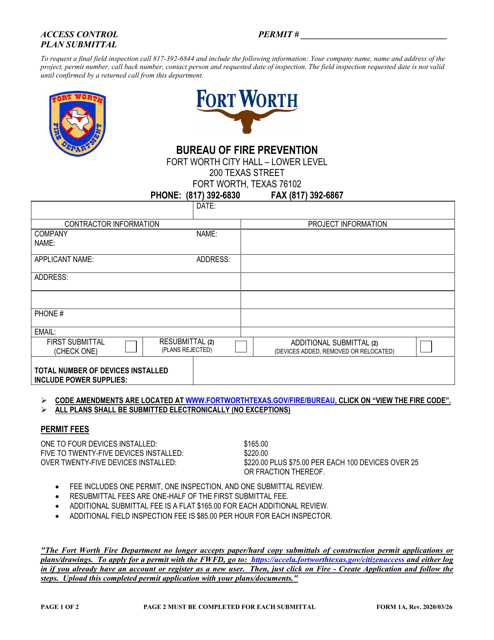
Municipalities, such as the City of Houston, Texas, also employ access control measures, implementing Security Control Plans to safeguard critical infrastructure and public spaces.
Overall, access control is a comprehensive and necessary system that ensures the security and safety of individuals, information, and assets. Effective access control measures, supported by various documentation such as access control forms, play a crucial role in regulating access to sensitive areas and maintaining the integrity of organizations and institutions.
Documents:
36
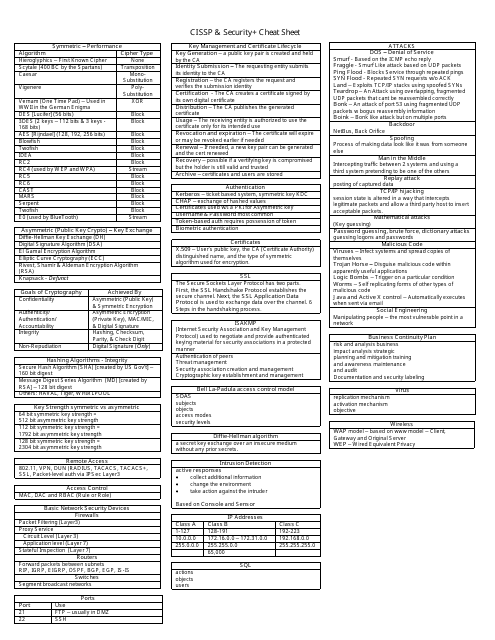
This document is a cheat sheet for the CISSP and Security+ certifications, providing quick reference information and tips for exam preparation.
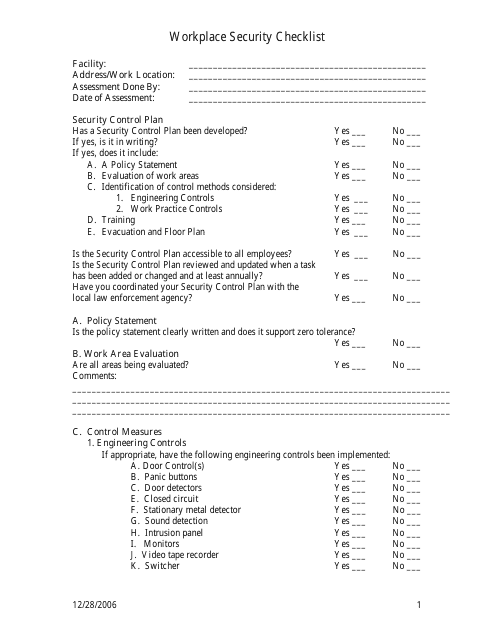
This document is a Workplace Security Checklist Template that can be used to assess the security measures and protocols in place at a workplace. It covers various areas such as access control, emergency preparedness, and physical security measures to ensure a safe and secure working environment.
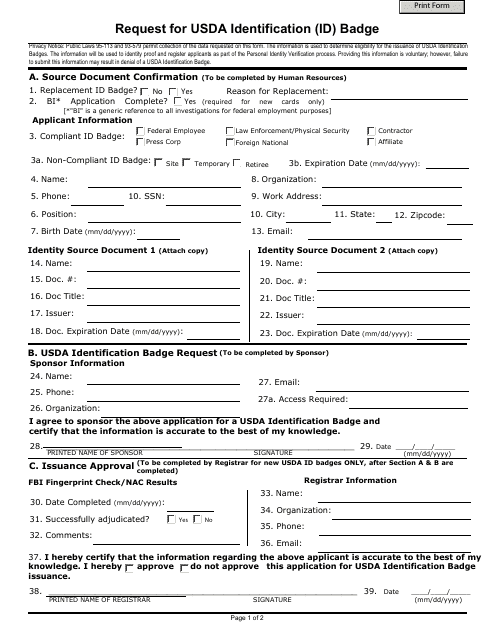
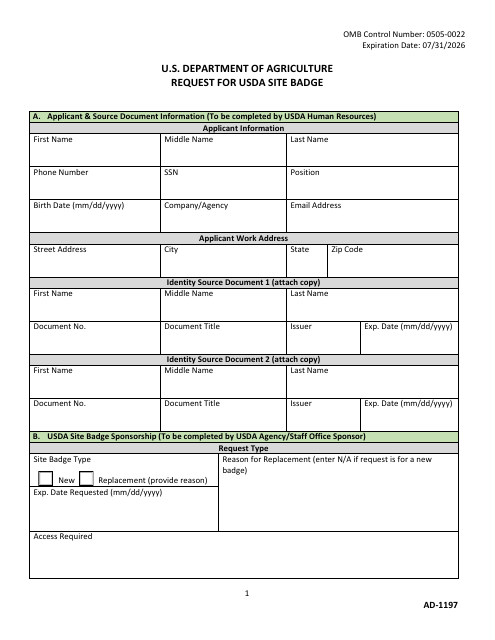
This form is used for requesting a USDA Identification (ID) Badge. It is required for accessing USDA facilities and resources.
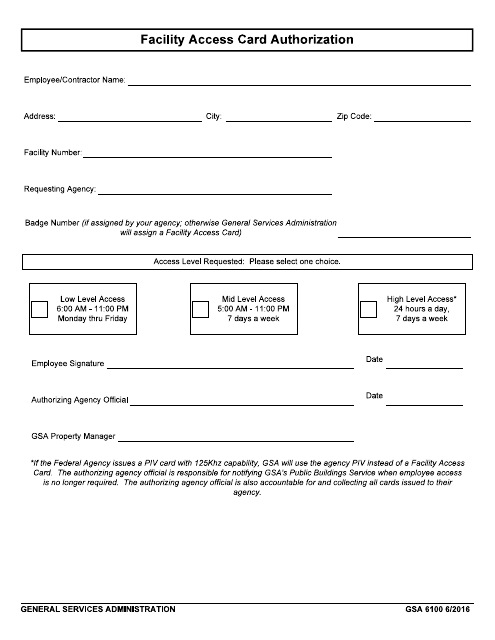
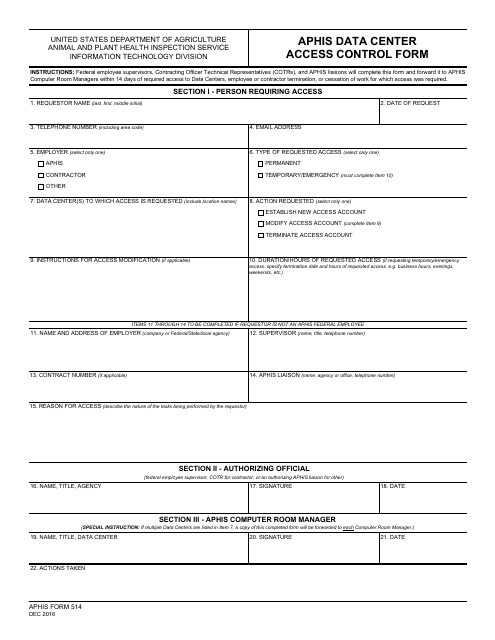
This Form is used for authorizing and issuing facility access cards for government employees and contractors.
This document is used in Maryland for transferring or authorizing the use of property within a government organization.
This document is for disabling, removing access, or reporting a lost access card in Vermont.
This form is used for certifying access to Sensitive Compartmented Information (SCI). It ensures that individuals are authorized to access classified information at a high level of security.
This form is used for providing notification for the ACS Access Control System in Montana.
This Form is used for requesting approval for a Protected Distribution System in the military.
This document is used for transferring ownership of property in Alaska and includes specific details about the property, such as whether it has frontage road access or is partially owned.
This form is used for transferring the ownership of a property with controlled access in Alaska.
This Form is used for transferring ownership of real estate from a corporation in Alaska. It includes provisions for a warranty of title and restrictions on access to the property.
This form is used for filing a warranty deed for standard or partial property with controlled access but without a frontage road in Alaska.
This document provides guidelines and best practices for enhancing the cybersecurity of industrial control systems using defense-in-depth strategies. It helps to protect critical infrastructure from cyber threats.
This handbook provides guidance on how to protect private and personal information from unauthorized access or disclosure. It covers best practices for safeguarding sensitive personally identifiable information.
This form is used for individuals or organizations in South Dakota who want to apply for relinquishment of access control. It is also known as SD Form 2233.
This document is used to grant limited access authorization to aliens and foreign nationals. It is used to ensure that these individuals have the necessary security clearance to access certain restricted areas or information.
This document is used to authorize access to a sub vault in West Virginia.
This Form is used for submitting an Access Control Plan to the City of Fort Worth, Texas.
This document outlines the security measures and protocols implemented by the City of Houston, Texas to protect its residents, infrastructure, and sensitive information. It provides a detailed plan for ensuring the safety and confidentiality of city operations.
This document is for a private club in Arizona that has a locked front door. It may include information about access procedures or rules for club members.
This document is an acknowledgement form used in Indiana for individuals or companies that rely on an ordinance to control access to groundwater.
This document provides a checklist for assessing the security measures in place at courthouses in Arizona. It helps to ensure the safety of individuals and the proper security protocols are followed.
This form is used for requesting a USDA site badge.