It Security Templates
Are you worried about the security of your IT systems? Protecting your sensitive data is a top priority for organizations of all sizes. That's why having a comprehensive IT security plan in place is crucial. Our IT security documents collection provides you with all the resources you need to assess vulnerabilities, manage risks, and implement strong security measures.
Our IT security documents cover a wide range of topics, including vulnerability assessments, risk assessments, and server vulnerability scans. These documents help you identify potential weaknesses in your IT infrastructure and take proactive steps to address them. By using our IT security templates, you can ensure that your organization is prepared to handle any potential security threats.
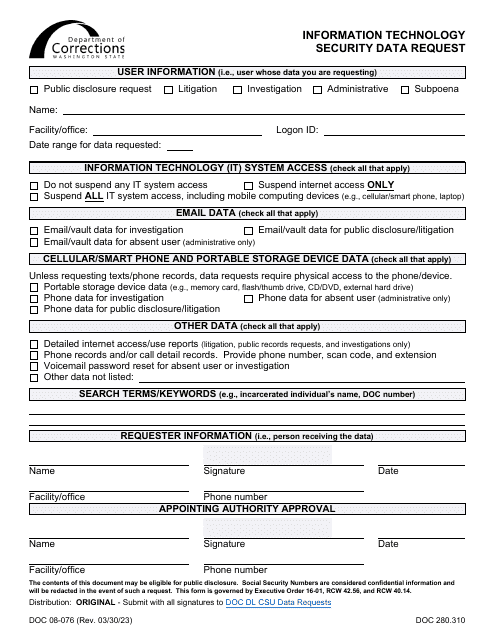
Additionally, our collection includes important forms and checklists related to IT security. These documents, such as the Information Technology Security Data Request and the Independent Security Audit Checklist, help you gather the necessary information and perform thorough security audits. This ensures that you are compliant with relevant regulations and industry best practices.
Whether you're a small business or a large enterprise, our IT security documents collection is designed to meet your specific needs. With our resources, you can strengthen your defenses, minimize the risk of data breaches, and protect your organization's reputation. Don't leave your IT security to chance - let our expertly crafted documents guide you towards a safer and more secure future.
Documents:
9
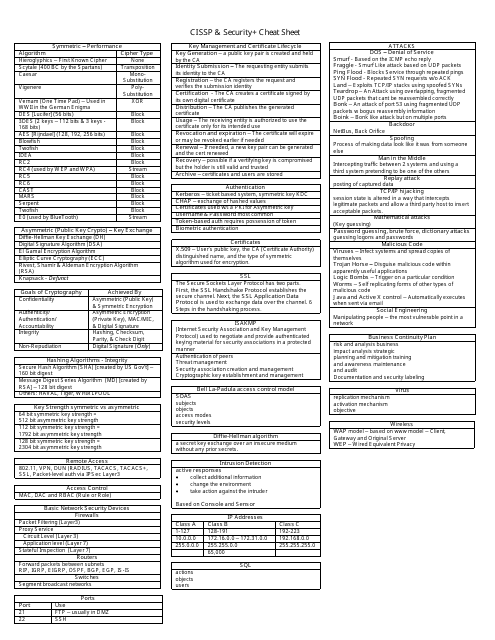
This document is a cheat sheet for the CISSP and Security+ certifications, providing quick reference information and tips for exam preparation.
This document is a template that is used to assess vulnerabilities in a system or network. It provides a structured approach to identify and analyze potential weaknesses, allowing for the development of effective mitigation strategies.
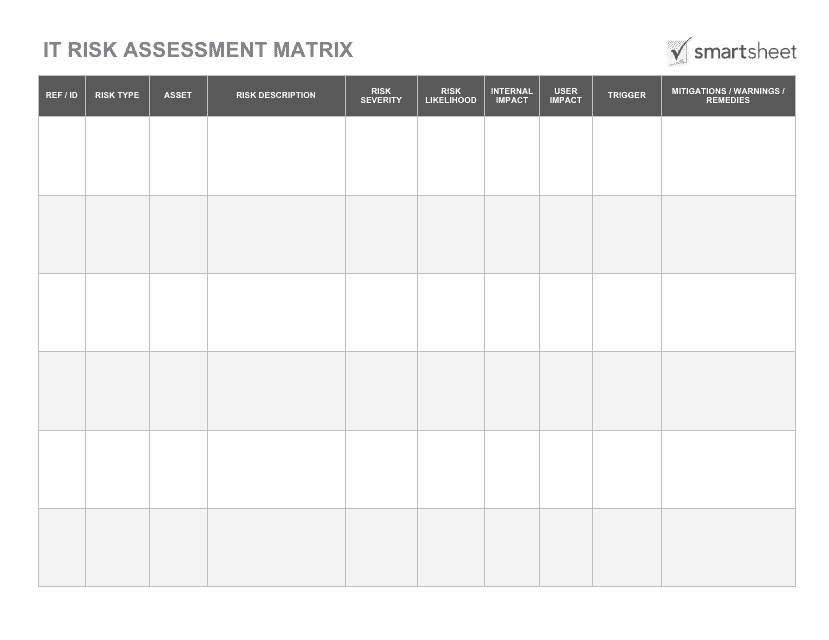
This document provides a template for conducting an IT risk assessment and creating a risk assessment matrix. It helps organizations identify and prioritize potential IT risks and take appropriate actions to mitigate them.
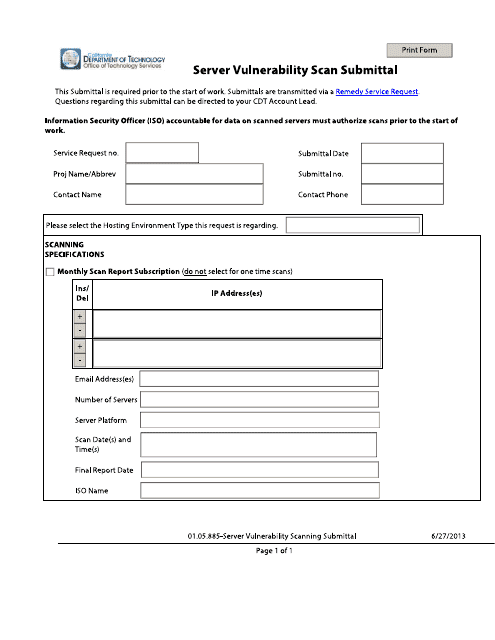
This Form is used for submitting a request for a vulnerability scan of a server in California.
This document is a checklist for conducting an independent security audit in Virginia. It provides guidance on evaluating the security measures in place and ensuring compliance with relevant laws and regulations.