Security Protocols Templates
Security protocols are essential for ensuring the confidentiality, integrity, and availability of sensitive information. These protocols establish a framework for implementing various security measures to protect valuable assets from unauthorized access, disclosure, or tampering. Security protocols are commonly referred to as security procedures or security measures and are crucial for organizations to mitigate the risks associated with potential security breaches.
Implementing effective security protocols involves a comprehensive approach that includes policies, guidelines, and procedures designed to safeguard information and resources. These protocols may include encryption, authentication, access control, and intrusion detection systems, among others. By following these protocols, organizations can minimize vulnerabilities, prevent data breaches, and maintain a secure environment.
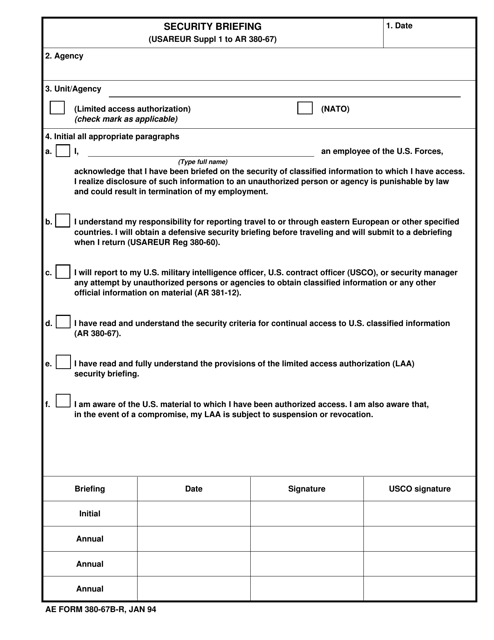
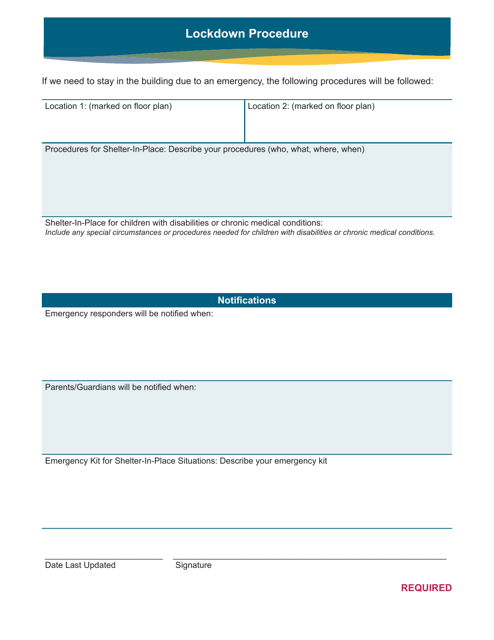
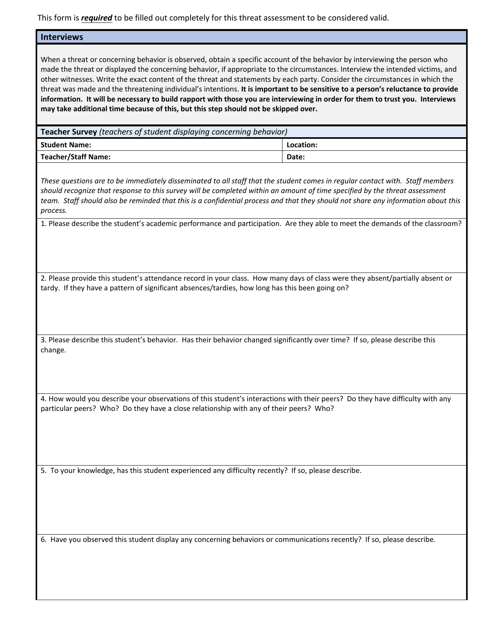
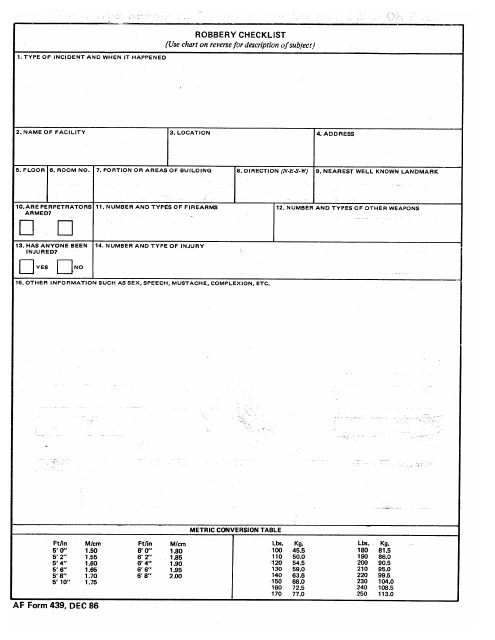
Examples of security protocols include DA Form 969 Top Secret Document Record, DA Form 2962 Security Termination Statement, AE Form 380-67B-R Security Briefing, DD Form 2965 Defense Sexual Assault Incident Database (Dsaid) Data Form, and Form CSO Court Security Officer Checklist - Kentucky. These documents are part of a collection that encompasses various measures and practices aimed at enhancing security and protecting sensitive information.
Security protocols play a crucial role in both government and non-government sectors, as they ensure the confidentiality and integrity of sensitive data. They are essential for organizations that handle sensitive information, such as defense agencies, financial institutions, healthcare providers, and research organizations. Adhering to these protocols is not only a best practice but also a legal requirement in many industries, as organizations must comply with various regulatory frameworks to protect sensitive information.
In conclusion, security protocols, also known as security procedures or security measures, are the cornerstone of a robust security framework. These protocols establish guidelines and practices to safeguard valuable assets from unauthorized access, disclosure, or tampering. By following these protocols, organizations can enhance their security posture and minimize the risks associated with potential security breaches.
Documents:
16
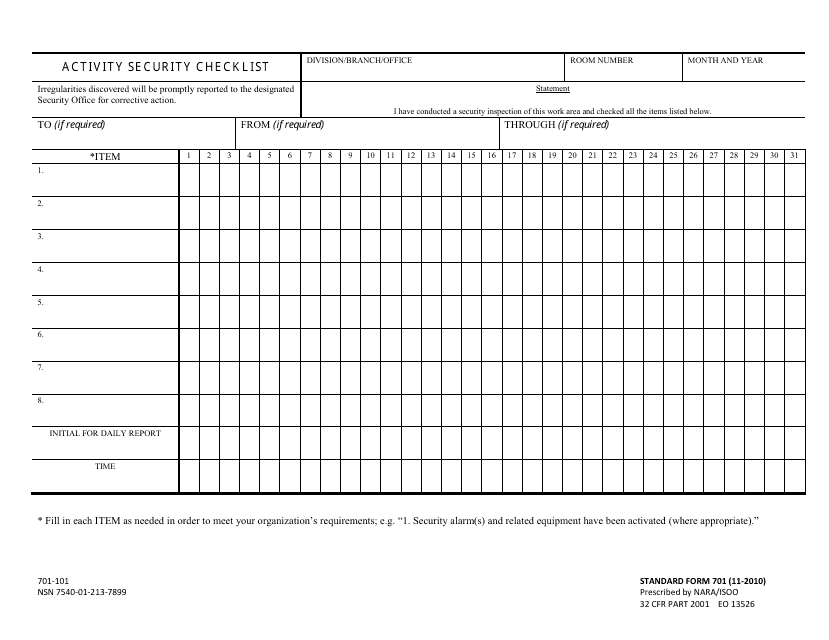
This form is used for conducting an activity security checklist, which is designed to ensure that proper security measures are in place and being followed. It is used to document the completion of security procedures and is typically used in government and military organizations.
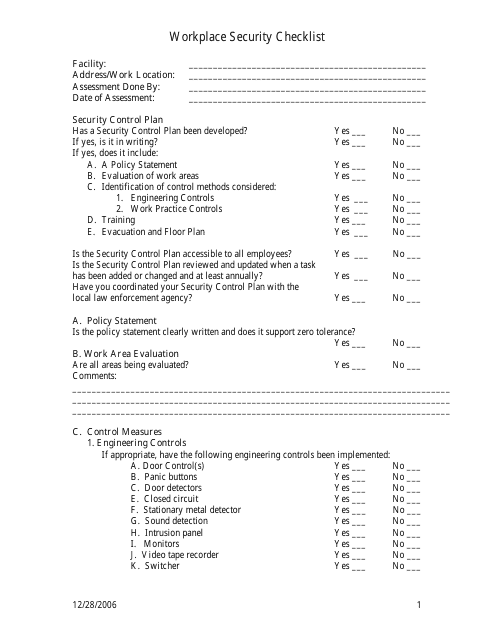
This document is a Workplace Security Checklist Template that can be used to assess the security measures and protocols in place at a workplace. It covers various areas such as access control, emergency preparedness, and physical security measures to ensure a safe and secure working environment.
This document provides a report on security awareness conducted by Sans, a trusted organization in the field of cybersecurity. It highlights key findings, trends, and recommendations to enhance security awareness.
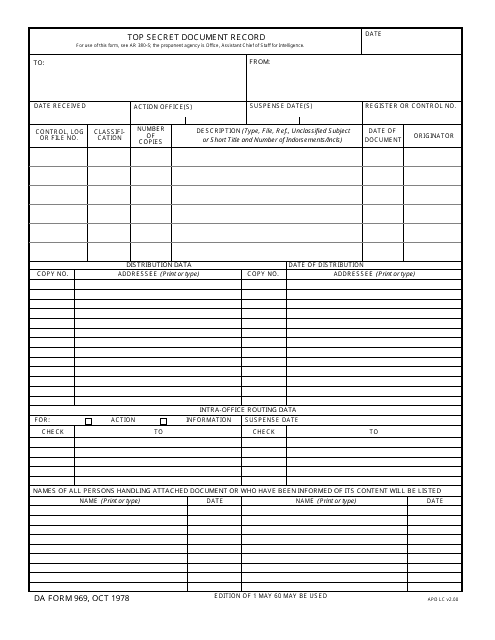
This Form is used for recording and tracking top secret documents in the US military.
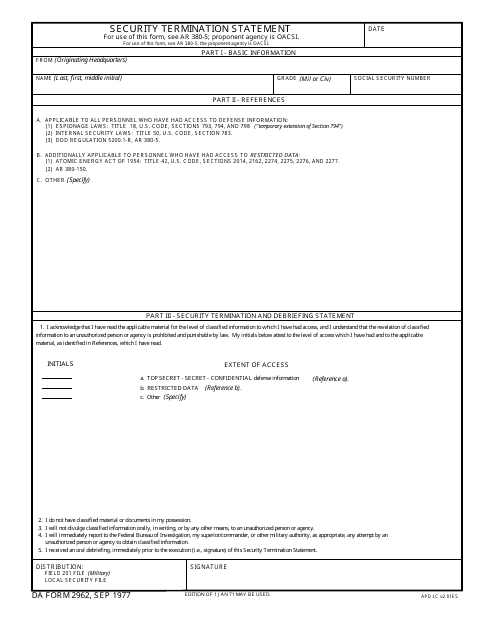
This form is used for submitting a security termination statement in the military.
This document provides guidelines and procedures for effectively responding to emergencies and ensuring security in the state of Arkansas. It covers various emergency scenarios and outlines the necessary steps to handle them.
This form is used for certifying access to Sensitive Compartmented Information (SCI). It ensures that individuals are authorized to access classified information at a high level of security.
This document is for conducting a security briefing in the U.S. Army. It provides guidelines and procedures for ensuring the security of sensitive information.
This guide provides information and guidelines for becoming a security guard in California. It covers the requirements, training, and licensing process to help individuals pursue a career in the field of security.
This form is used for requesting authorization to enter a close-in security area.
This document outlines the procedure to be followed during a lockdown situation in the state of Nebraska. It provides guidance on how to ensure the safety and security of individuals in various settings such as schools, offices, and public venues.
This Form is used for assessing potential threats in Wisconsin schools through a survey completed by teachers.
This document provides a checklist for assessing the security measures in place at courthouses in Arizona. It helps to ensure the safety of individuals and the proper security protocols are followed.
This form is used for the Court Security Officer Checklist in Kentucky to ensure the safety and security of the court premises.