Data Security Templates
In today's digital age, protecting sensitive data has become more crucial than ever before. With the rise of cyber threats and data breaches, organizations need to prioritize data security to safeguard both their own interests and the privacy of their customers.
Our data security documents collection provides a comprehensive set of resources to help you establish and maintain robust data protection measures. Whether you are an individual, small business, or a large corporation, our suite of documents offers invaluable guidance and tools to ensure the confidentiality, integrity, and availability of your data.
From risk management database forms to service backup plans, our documents cover a wide range of topics to address various aspects of data security. These resources not only facilitate compliance with regulatory requirements but also offer best practices and industry guidelines to enhance the security posture of your organization.
In addition to offering expertly crafted templates, our documents also keep you informed about the latest legal developments in the field of data security. Stay updated with mandatory data breach notifications in California, annual certification forms for insurance firms in Connecticut, and IRS agreements for secure messaging with designated users. With our documents, you can stay ahead of the curve and implement proactive measures to protect your valuable data from potential threats.
Don't leave your data vulnerable to unauthorized access or exploitation. Explore our comprehensive data security documents collection and empower yourself with the knowledge and resources needed to develop a robust data protection strategy. Safeguard your organization's reputation, maintain customer trust, and ensure compliance with the various data security regulations with our meticulously curated documents.
Trust our data security documents to be your go-to resource for all your data protection needs. Start fortifying your organization's data security practices today to protect your sensitive information from unauthorized access, data breaches, and other potential threats.
Documents:
66
This Form is used for reporting data incidents to the IRS Office of Safeguards in California. It is used to notify the IRS of any unauthorized disclosure, loss, or theft of taxpayer information.
This form is used for requesting access to data security in California by Hhsdc Teale.
This form is used for requesting information on the disclosure of personal information in the state of California.
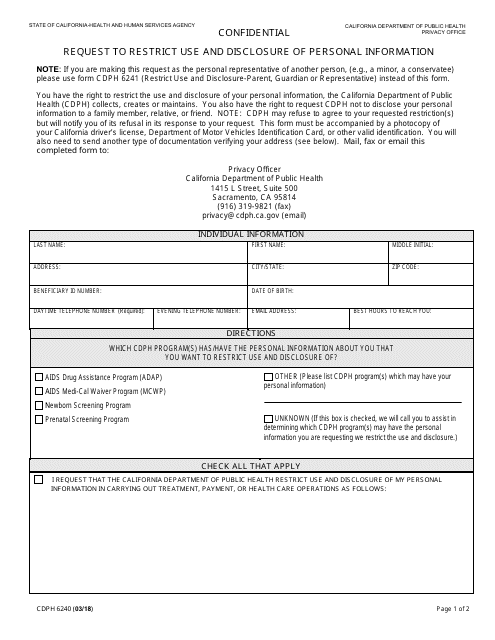
This form is used for requesting to restrict the use and disclosure of personal information in the state of California.
This document is used to pledge your commitment to information security awareness in the state of Florida. It helps promote awareness and education about protecting sensitive information.
This document is a confidentiality agreement form specific to the state of Montana. It is used in accordance with the Health Insurance Portability and Accountability Act (HIPAA) to ensure the protection of personal health information.
This document is a Data License Agreement for the Nevada Natural Heritage Program in Nevada. It outlines the terms and conditions for the use of data from the program.
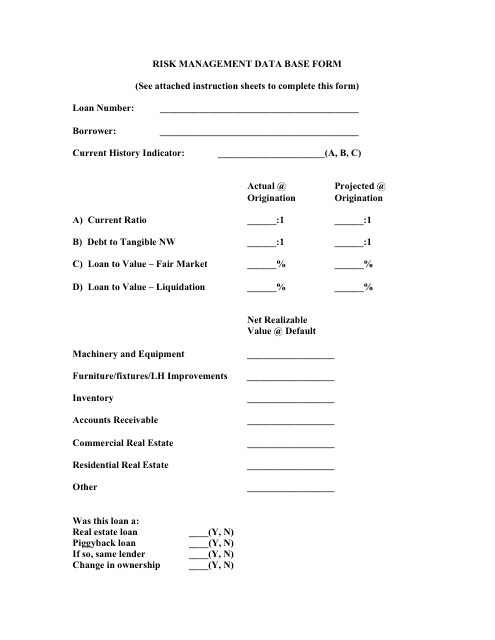
This Form is used for collecting and organizing data related to risk management. It helps businesses or organizations track and analyze potential risks, identify trends, and develop effective strategies to mitigate them.
This checklist is used for managed care organizations operating in the state of Delaware. It includes requirements and guidelines for compliance and best practices in managing care for patients.
This document is a Privacy Policy Notice specifically applicable to residents of South Carolina. It outlines how personal information is collected, used, and protected by companies operating in South Carolina.
This document provides guidelines and restrictions for the usage of personal electronic devices in Nunavut, Canada. It outlines the rules and expectations that individuals must adhere to when using their personal electronic devices in various settings.
This document is used for requesting the removal of personal information in the state of Ohio.
This document is used for granting access to individual records in the state of Minnesota.
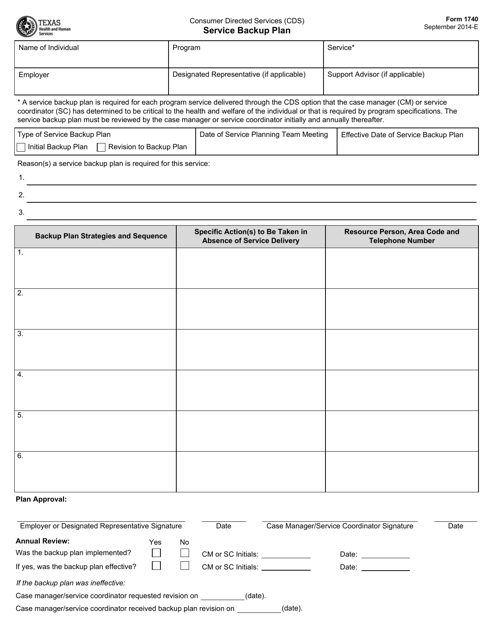
This form is used for creating a service backup plan specific to the state of Texas. It helps in ensuring the continuity of services in case of emergencies or disruptions.
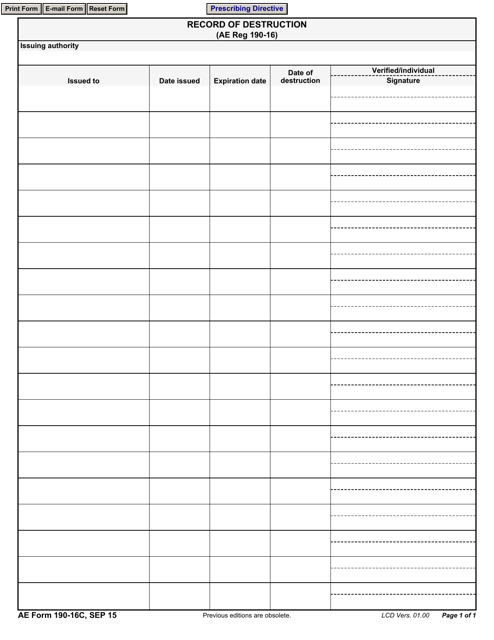
This form is used for recording the destruction of certain items or materials. It helps keep track of what was destroyed and when.
This agreement between an employer and their worker enables the employee to work at a place different from the primary business location and helps an employer cut down on costs.
This Document outlines the terms and conditions for the licensing of digital data in Nevada.
This document outlines the agreement for accessing and using information in the state of California. It sets out the terms and conditions for how information can be accessed, shared, and used within the state.
This document is used for requesting security authorization in the state of Virginia. It helps ensure the safety and protection of individuals and businesses.
This Form is used for managing remote user security rights and maintaining confidentiality in the state of Texas.
This form is used for requesting data related to HIV/STD services in Oklahoma. It allows individuals to submit a formal request to access specific information or statistics regarding HIV/STD prevention, testing, and treatment services in the state.
This document is a sample agreement for the use of an encrypted flash drive in South Carolina. It outlines the terms and conditions for the use and protection of the flash drive to ensure the security of stored information.
This type of assessment refers to a system of evaluating the security of a company following the regulations established by the National Institute of Standards and Technology (NIST)
This document acts as a documented process of identifying flaws and introducing safety measures to protect a health organization.
This document is used for certifying an information security program in accordance with the Louisiana Insurance Data Security Law.
This form is used for obtaining an exemption certification for the Information Security Program under the Louisiana Insurance Data Security Law.
This document certifies the destruction of records in the state of Kentucky. It provides proof that sensitive or confidential information has been properly disposed of.
This Form is used for reporting a security breach and notifying the Delaware authorities.
This type of document is a security addendum for the Federal Bureau of Investigation's Criminal Justice Information Services in New Hampshire.
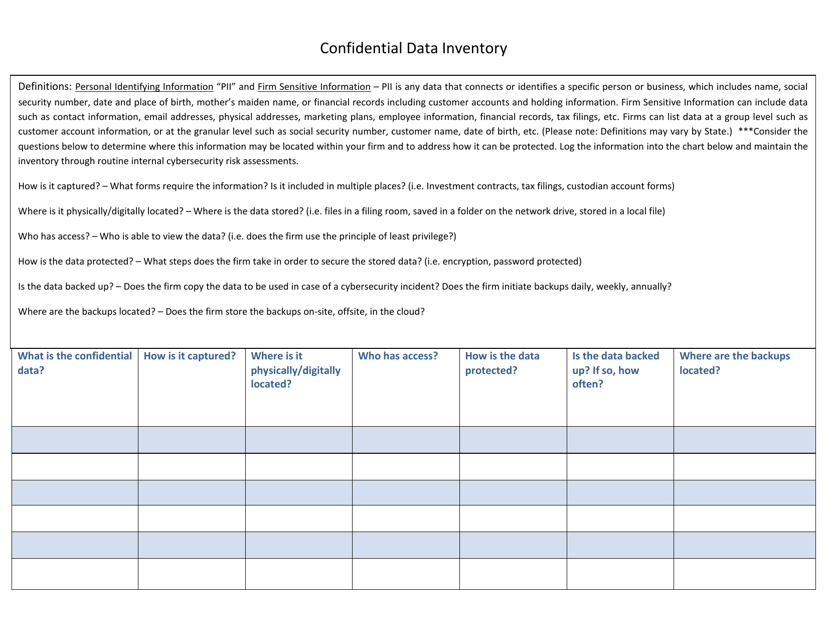
This document is used to keep track of confidential data stored in Ohio.
This form is used for authorizing the IRS to disclose taxpayer information to designated users through secure messaging.
This document is used for requesting an exemption from the requirement to protect personal information for covered employees in the state of Florida. It outlines the protocols that need to be followed to protect personal information.
This document outlines the policies and guidelines regarding the use of information technology resources in Iowa. It covers topics such as acceptable use, security practices, and consequences for violating the policy.